Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
Valid Microsoft MS-500 questions shared by Pass4itsure for helping to pass the Microsoft MS-500 exam! Get the newest Pass4itsure Microsoft MS-500 exam dumps with VCE and PDF here: https://www.pass4itsure.com/ms-500.html (208 Q&As Dumps).
[Free PDF] Microsoft MS-500 pdf Q&As https://drive.google.com/file/d/1fr3kpN_qJjcgd6Z8ey_PoNQ7TWdRqSrq/view?usp=sharing
Suitable for MS-500 complete Microsoft learning pathway
The content is rich and diverse, and learning will not become boring. You can learn in multiple ways through the Microsoft MS-500 exam.
Microsoft MS-500 Microsoft 365 Security Administration
- Download
- Answer practice questions, the actual Microsoft MS-500 test
Free Microsoft MS-500 dumps download
[PDF] Free Microsoft MS-500 dumps pdf download https://drive.google.com/file/d/1fr3kpN_qJjcgd6Z8ey_PoNQ7TWdRqSrq/view?usp=sharing
Pass4itsure offers the latest Microsoft MS-500 practice test free of charge 1-13
QUESTION 1
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains
a unique solution that might meet the stated goals. Some question sets might have more than one correct solution,
while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not
appear in the review screen.
You have an on-premises Active Directory domain named contoso.com.
You install and run Azure AD Connect on a server named Server1 that runs Windows Server.
You need to view Azure AD Connect events.
You use the Directory Service event log on Server1.
Does that meet the goal?
A. Yes
B. No
Correct Answer: B
References: https://support.pingidentity.com/s/article/PingOne-How-to-troubleshoot-an-AD-Connect-Instance
QUESTION 2
You have a Microsoft 365 subscription.
You create a supervision policy named Policy1, and you designate a user named User1 as the reviewer.
What should User1 use to view supervised communications?
A. a team in Microsoft Teams
B. the Security and Compliance admin center
C. Outlook on the web
D. the Exchange admin center
Correct Answer: B
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/supervision-policies?view=o365-worldwide
QUESTION 3
You need to recommend a solution to protect the sign-ins of Admin1 and Admin2. What should you include in the recommendation?
A. a device compliance policy
B. an access review
C. a user risk policy
D. a sign-in risk policy
Correct Answer: C
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-user-risk-policy
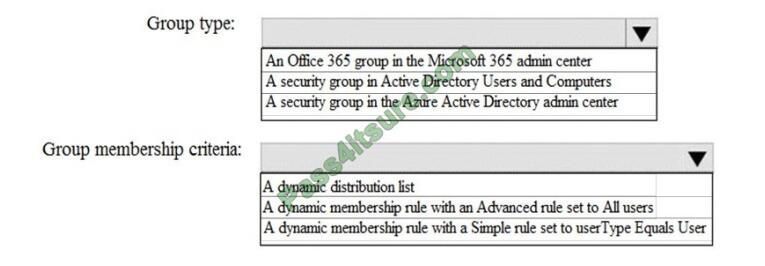
QUESTION 4
HOTSPOT
How should you configure Group3? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point. Hot Area:
Correct Answer:
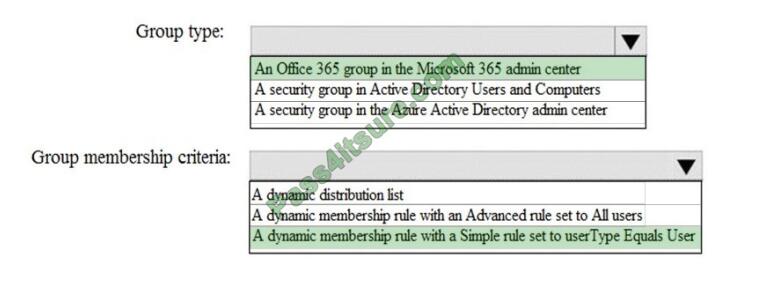
QUESTION 5
You have a Microsoft 365 subscription.
You need to ensure that users can manually designate which content will be subject to data loss prevention (DLP)
policies.
What should you create first?
A. A retention label in Microsoft Office 365
B. A custom sensitive information type
C. A Data Subject Request (DSR)
D. A safe attachments policy in Microsoft Office 365
Correct Answer: C
References: https://docs.microsoft.com/en-us/office365/securitycompliance/manage-gdpr-data-subject-requests-withthe-dsr-case-tool#more-information-about-using-the-dsr-case-tool
QUESTION 6
You have a hybrid Microsoft 365 environment.
All computers run Windows 10 Enterprise and have Microsoft Office 365 ProPlus installed. All the computers are joined
to Active Directory.
You have a server named Server1 that runs Windows Server 2016. Server1 hosts the telemetry database. You need to
prevent private details in the telemetry data from being transmitted to Microsoft.
What should you do?
A. On Server1, run readinessreportcreator.exe
B. Configure a registry entry on Server1
C. Configure a registry entry on the computers
D. On the computers, run tdadm.exe
Correct Answer: C
“To allow yourself and other administrators to identify the owners of Office files that have compatibility issues without
revealing file names or specific locations, you can enable file obfuscation, which disguises Office file names, titles, and
file paths. This setting is configured on the agent, which performs the obfuscation task before uploading data to the
shared folder. The data that is stored on the local computer is not obfuscated.”
https://docs.microsoft.com/enus/deployoffice/compat/manage-the-privacy-of-data-monitored-by-telemetry-in-office
QUESTION 7
You have a Microsoft 365 subscription.
You enable auditing for the subscription.
You plan to provide a user named Auditor with the ability to review audit logs.
You add Auditor to the Global administrator role group.
Several days later, you discover that Auditor disabled auditing.
You remove the Auditor from the Global administrator role group and enable auditing.
You need to modify Auditor to meet the following requirements:
1.
Be prevented from disabling auditing
2.
Use the principle of least privilege
3.
Be able to review the audit log
To which role group should you add Auditor?
A. Security reader
B. Compliance administrator
C. Security operator
D. Security administrator
Correct Answer: C
References: https://docs.microsoft.com/en-us/office365/securitycompliance/permissions-in-the-security-and-compliancecenter
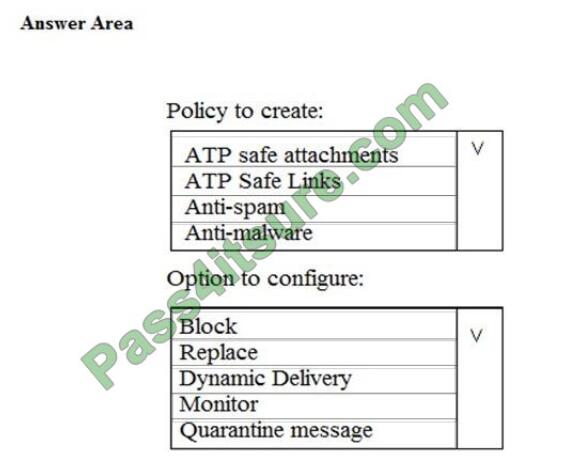
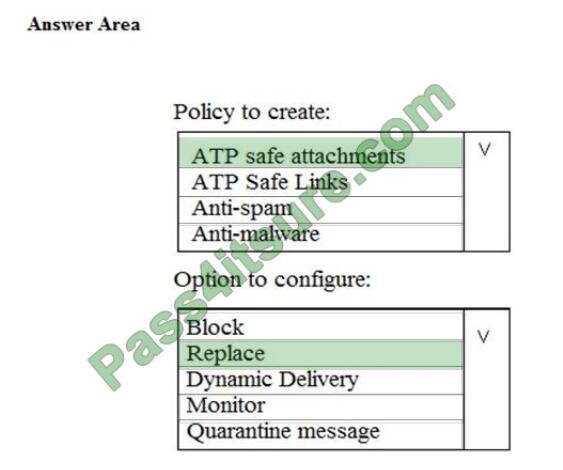
QUESTION 8
You need to recommend an email malware solution that meets the security requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
QUESTION 9
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains
a unique solution that might meet the stated goals. Some question sets might have more than one correct solution,
while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not
appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in Security and Compliance to identify who signed in to the mailbox of User1, the results
are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
You run the Set-Maibox -Identity “User1” -AuditEnabled $true command.
Does that meet the goal?
A. Yes
B. No
Correct Answer: A
References: https://docs.microsoft.com/en-us/powershell/module/exchange/mailboxes/set-mailbox?view=exchange-ps
QUESTION 10
HOTSPOT
You install Azure ATP sensors on domain controllers.
You add a member to the Domain Admins group. You view the timeline in Azure ATP and discover that information
regarding the membership change is missing.
You need to meet the security requirements for Azure ATP reporting.
What should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
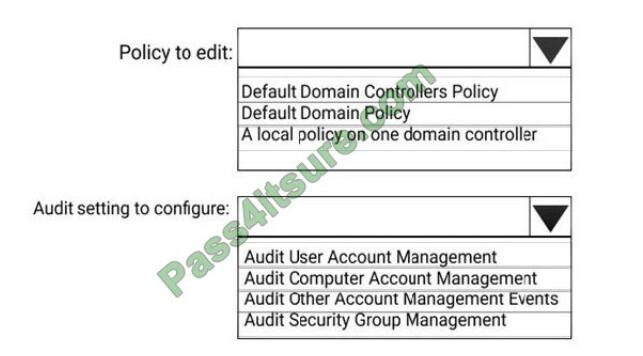
Correct Answer:
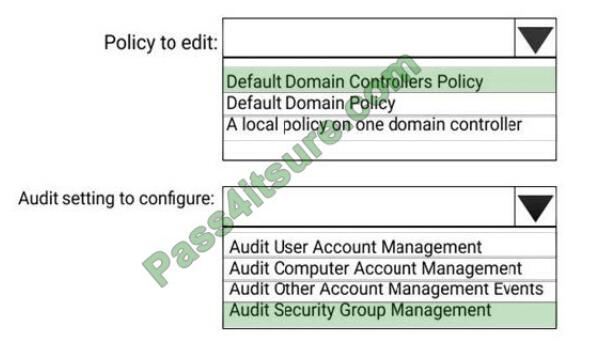
References: https://docs.microsoft.com/en-us/azure-advanced-threat-protection/atp-advanced-audit-policy
QUESTION 11
You need to protect against phishing attacks. The solution must meet the following requirements:
1.
Phishing email messages must be quarantined if the messages are sent from a spoofed domain.
2.
As many phishing email messages as possible must be identified.
The solution must apply to the current SMTP domain names and any domain names added later.
To complete this task, sign in to the Microsoft 365 admin center. Correct Answer: See below.
1.
After signing in to the Microsoft 365 admin center, select Security, Threat Management, Policy, then ATP Antiphishing.
2.
Select Default Policy to refine it.
3
In the Impersonation section, select Edit.
4.
Go to Add domains to protect and select the toggle to automatically include the domains you own.
5.
Go to Actions, open the drop-down If email is sent by an impersonated user, and choose the Quarantine message
action. Open the drop-down If an email is sent by an impersonated domain and choose the Quarantine message action.
6.
Select Turn on impersonation safety tips. Choose whether tips should be provided to users when the system detects
impersonated users, domains, or unusual characters. Select Save.
7.
Select Mailbox intelligence and verify that it\\’s turned on. This allows your email to be more efficient by learning usage
patterns.
8.
Choose to Add trusted senders and domains. Here you can add email addresses or domains that shouldn\\’t be classified
as an impersonation.
9.
Choose Review your settings, make sure everything is correct, select Save, then Close.
Reference: https://support.office.com/en-us/article/protect-against-phishing-attempts-inmicrosoft-365-86c425e1-1686-430a-9151-f7176cce4f2c#ID0EAABAAA=Try_it!
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/set-up-anti-phishingpolicies?view=o365-worldwide#example-anti-phishing-policy-to-protect-a-user-and-a-domain
QUESTION 12
You have a Microsoft 365 subscription linked to an Azure Active Directory (Azure AD) tenant that contains a user named
User1.
You have a Data Subject Request (DSR) case named Case1.
You need to allow User1 to export the results of Case1. The solution must use the principle of least privilege.
Which role should you assign to User1 for Case1?
A. eDiscovery Manager
B. Security Operator
C. eDiscovery Administrator
D. Global Reader
Correct Answer: A
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/manage-gdpr-data-subject-requests-with-the-dsrcase-tool?view=o365-worldwide#step-1-assign-ediscovery-permissions-to-potential-case-members
QUESTION 13
Your network contains an on-premises Active Directory domain. The domain contains servers that run Windows Server
and have advanced auditing enabled.
The security logs of the servers are collected by using a third-party SIEM solution.
You purchase a Microsoft 365 subscription and plan to deploy Azure Advanced Threat Protection (ATP) by using
standalone sensors.
You need to ensure that you can detect when sensitive groups are modified and when malicious services are created.
What should you do?
A. Configure auditing in the Office 365 Security and Compliance center.
B. Turn off Delayed updates for the Azure ATP sensors.
C. Modify the Domain synchronizer candidate\\’s settings on the Azure ATP sensors.
D. Integrate SIEM and Azure ATP.
Correct Answer: D
References: https://docs.microsoft.com/en-us/azure-advanced-threat-protection/install-atp-step5
Pass4itsure Microsoft exam dumps discount code share

Summarize:
[Q1-Q13] Free Microsoft MS-500 pdf download https://drive.google.com/file/d/1fr3kpN_qJjcgd6Z8ey_PoNQ7TWdRqSrq/view?usp=sharing
Share all the resources: Latest Microsoft MS-500 practice questions, latest Microsoft MS-500 pdf dumps. The latest updated Microsoft MS-500 dumps https://www.pass4itsure.com/ms-500.html Study hard and practices a lot. This will help you prepare for the Microsoft MS-500 exam. Good luck!
Related
Discover more from Exampass: Collection of Cisco (CCNA, CCNP, Meraki Solutions Specialist, CCDP...) exam questions and answers from Pass4itsure
Subscribe to get the latest posts sent to your email.
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

