Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)

CCNP Security 350-701 dumps are the best exam material based on Cisco’s knowledge of implementing and operating core security technologies!
CCNP Security 350-701 exam “Implementing and Operating Cisco Security Core Technologies (SCOR)” covers network security, cloud security, content security, endpoint protection and detection, secure network access, visibility, and enforcement A Comprehensive Exam of Exam Topics!
The CCNP Security 350-701 dumps exam material contains 598 up-to-date exam questions and answers that fully match the CCNP Security 350-701 exam topics!
Download CCNP Security 350-701 dumps: https://www.leads4pass.com/350-701.html, using PDF and VCE to help you easily practice to pass the exam successfully.
Experience some of the latest CCNP Security 350-701 dumps exam questions online:
| From | Number of exam questions | Associated certifications | Online download | Last updated |
| Pass4itsure | 13 | CCNP Security | 350-701 PDF | 350-701 dumps |
NEW QUESTION 1:
What provides total management for mobile and PC including managing inventory and device tracking, remote view, and live troubleshooting using the included native remote desktop support?
A. mobile device management
B. mobile content management
C. mobile application management
D. mobile access management
Correct Answer: A
NEW QUESTION 2:
What is the process of performing automated static and dynamic analysis of files against preloaded behavioral
indicators for threat analysis?
A. deep visibility scan
B. point-in-time checks
C. advanced sandboxing
D. advanced scanning
Correct Answer: C
NEW QUESTION 3:
What are the two functions of IKEv1 but not IKEv2? (Choose two.)
A. IKEv1 conversations are initiated by the IKE_SA_INIT message.
B. With IKEv1, the aggressive mode negotiates faster than the main mode.
C. IKEv1 uses EAP for authentication.
D. NAT-T is supported in IKEv1 but not in IKEv2.
E. With IKEv1, when using the aggressive mode, the initiator and responder identities are passed in cleartext.
Correct Answer: BE
Reference: https://community.cisco.com/t5/routing/internet-key-exchange-ike-aggressive-mode/td-p/2081283
NEW QUESTION 4:
Which service allows a user to export application usage and performance statistics with Cisco Application Visibility and Control?
A. SNORT
B. NetFlow
C. SNMP
D. 802.1X
Correct Answer: B
Application Visibility and Control (AVC) supports NetFlow to export application usage and performance statistics. This data can be used for analytics, billing, and security policies.
NEW QUESTION 5:
An engineer wants to generate NetFlow records on traffic traversing the Cisco ASA. Which Cisco ASA command must be used?
A. flow-export destination inside 1.1.1.1 2055
B. B. ip flow monitor input
C. ip flow-export destination 1.1.1.1 2055
D. flow exporter
Correct Answer: A
NEW QUESTION 6:
Refer to the exhibit.
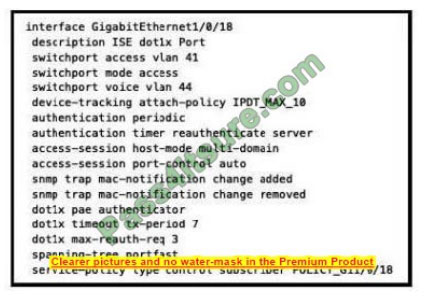
What will occur when this device tries to connect to the port?
A. 802.1X will not work, but MAB will start and allow the device on the network.
B. 802.1X will not work and the device will not be allowed network access
C. 802 1X will work and the device will be allowed on the network
D. 802 1X and MAB will both be used and ISE can use policy to determine the access level
Correct Answer: B
NEW QUESTION 7:
Which action must be taken in the AMP for the Endpoints console to detect specific MD5 signatures on endpoints and then quarantine the files?
A. Configure an advanced custom detection list.
B. Configure an IP Block and Allow a custom detection list
C. Configure an application custom detection list
D. Configure a simple custom detection list
Correct Answer: A
NEW QUESTION 8:
Which suspicious pattern enables the Cisco Tetration platform to learn the normal behavior of users?
A. file access from a different user
B. interesting file access
C. user login suspicious behavior
D. privilege escalation
Correct Answer: C
NEW QUESTION 9:
An engineer integrates Cisco FMC and Cisco ISE using pxGrid. Which role is assigned to Cisco FMC?
A. client
B. server
C. controller
D. publisher
Correct Answer: D
NEW QUESTION 10:
What must be enabled to secure SaaS-based applications?
A. modular policy framework
B. two-factor authentication
C. application security gateway
D. end-to-end encryption
Correct Answer: C
NEW QUESTION 11:
How does Cisco Workload Optimization Manager help mitigate application performance issues?
A. It deploys an AWS Lambda system
B. It automates resource resizing
C. It optimizes a flow path
D. It sets up a workload forensic score
Correct Answer: B
NEW QUESTION 12:
What are two rootkit types? (Choose two)
A. registry
B. virtual
C. bootloader
D. user mode
E. buffer mode
Correct Answer: CD
The term rootkit\\' originally comes from the Unix world, where the wordroot\’ is used to describe a user with the highest possible level of access privileges, similar to an Administrator\\’ in Windows. The wordkit\’ refers to the software that grants root-level access to the machine. Put the two together and you get `rootkit\’, a program that gives someone? with legitimate or malicious intentions? privileged access to a computer.
There are four main types of rootkits: Kernel rootkits, User mode rootkits, Bootloader rootkits, Memory rootkits
NEW QUESTION 13:
An engineer is implementing NTP authentication within their network and has configured both the client and server devices with the command NTP authentication-key 1 md5 Cisc392368270. The server at 1.1.1.1 is attempting to authenticate to the client at 1.1.1.2, however, it is unable to do so. Which command is required to enable the client to accept the server\’s authentication key?
A. NTP peer 1.1.1.1 key 1
B. NTP server 1.1.1.1 key 1
C. NTP server 1.1.1.2 key 1
D. NTP peer 1.1.1.2 key 1
Correct Answer: B
To configure an NTP-enabled router to require authentication when other devices connect to it, use the following
commands:NTP_Server(config)#ntp authentication-key 2 md5 securitytutNTP_Server(config)#ntp
authenticateNTP_Server (config)#ntp trusted-key 2 Then you must configure the same authentication key on the client
router:NTP_Client(config)#ntp authentication-key 2 md5 securitytutNTP_Client(config)#ntp
authenticateNTP_Client(config)#ntp trusted-key 2NTP_Client(config)#ntp server 10.10.10.1 key 2Note: To configure a Cisco device as an NTP client, use the command NTP server. For example Router(config)#ntp server 10.10.10.1. This command will instruct the router to query 10.10.10.1 for the time.
…
This online practice helps you really understand the latest CCNP Security 350-701 exam “Implementing and Operating Cisco Security Core Technologies (SCOR)”!
CCNP Security 350-701 exam belongs to the CCNP Security core exam, so the exam is relatively difficult, and it will be easier for experienced candidates! But with the update of exam materials, it is a new challenge for everyone!
Download CCNP Security 350-701 dumps exam material: https://www.leads4pass.com/350-701.html, to help candidates of any learning level learn easily, complete challenges, and pass the exam successfully!
Related
Discover more from Exampass: Collection of Cisco (CCNA, CCNP, Meraki Solutions Specialist, CCDP...) exam questions and answers from Pass4itsure
Subscribe to get the latest posts sent to your email.
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

