Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
Pass4itsure share these resources with you. Both VCE and PDF dumps contain the latest Cisco 350-701 exam questions, which will ensure your 350-701 exam 100% passed! You can get 350-701 VCE dumps and 350-701 PDF dumps from Pass4itsure. Please get the latest Pass4itsure 350-701 dumps here: https://www.pass4itsure.com/350-701.html (155 QA Dumps).
Download The Real Cisco 350-701 PDF Here, Free
[free pdf] Cisco 350-701 PDF [Drive] https://drive.google.com/file/d/1fQK_2JniBT9g4KxlZkQDKu6SzXHmfRFQ/view?usp=sharing
Cisco CCNP 350-701 Practice Test Questions Answers
QUESTION 1
What is the difference between deceptive phishing and spear phishing?
A. Deceptive phishing is an attack aimed at a specific user in the organization who holds a C-level role.
B. A spear-phishing campaign is aimed at a specific person versus a group of people.
C. Spear phishing is when the attack is aimed at the C-level executives of an organization.
D. Deceptive phishing hijacks and manipulates the DNS server of the victim and redirects the user to a false webpage.
Correct Answer: B
QUESTION 2
A network administrator configures Dynamic ARP Inspection on a switch. After Dynamic ARP Inspection is applied, all
users on that switch are unable to communicate with any destination. The network administrator checks the interface
status of all interfaces, and there is no err-disabled interface.
What is causing this problem?
A. The ip arp inspection limit command is applied on all interfaces and is blocking the traffic of all users.
B. DHCP snooping has not been enabled on all VLANs.
C. The no ip arp inspection trust command is applied on all user host interfaces
D. Dynamic ARP Inspection has not been enabled on all VLANs
Correct Answer: C
QUESTION 3
What must be used to share data between multiple security products?
A. Cisco Stealthwatch Cloud
B. Cisco Advanced Malware Protection
C. Cisco Platform Exchange Grid
D. Cisco Rapid Threat Containment
Correct Answer: C
QUESTION 4
An engineer needs a solution for TACACS+ authentication and authorization for device administration. The engineer
also wants to enhance wired and wireless network security by requiring users and endpoints to use 802.1X, MAB, or
WebAuth. Which product meets all of these requirements?
A. Cisco Prime Infrastructure
B. Cisco Identity Services Engine
C. Cisco Stealthwatch
D. Cisco AMP for Endpoints
Correct Answer: B
QUESTION 5
DRAG DROP
Drag and drop the steps from the left into the correct order on the right to enable AppDynamics to monitor an EC2
an instance in Amazon Web Services.
Select and Place:
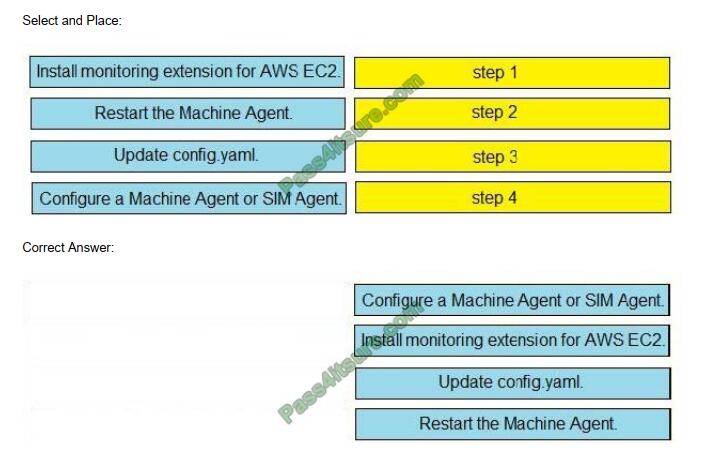
QUESTION 6
Which three statements about the VRF-Aware Cisco Firewall are true? (Choose three)
A. It supports both global and per-VRF commands and DoS parameters.
B. It enables service providers to deploy firewalls on customer devices.
C. It can generate Syslog massages that are visible only to individual VPNs.
D. It can support VPN networks with overlapping address ranges without NAT.
E. It enables service providers to implement firewalls on PE devices.
F. It can run as more than one instance.
Correct Answer: CEF
QUESTION 7
Which technology is used to improve web traffic performance by proxy caching?
A. WSA
B. Firepower
C. FireSIGHT
D. ASA
Correct Answer: A
QUESTION 8
What is the result of running the crypto isakmp key ciscXXXXXXXX address 172.16.0.0 command?
A. authenticates the IKEv2 peers in the 172.16.0.0/16 range by using the key ciscXXXXXXXX
B. authenticates the IP address of the 172.16.0.0/32 peer by using the key ciscXXXXXXXX
C. authenticates the IKEv1 peers in the 172.16.0.0/16 range by using the key ciscXXXXXXXX
D. secures all the certificates in the IKE exchange by using the key ciscXXXXXXXX
Correct Answer: B
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/security/a1/sec-a1-cr-book/sec-crc4.html#wp6039879000
QUESTION 9
Which two deployment model configurations are supported for Cisco FTDv in AWS? (Choose two.)
A. Cisco FTDv configured in routed mode and managed by an FMCv installed in AWS
B. Cisco FTDv with one management interface and two traffic interfaces configured
C. Cisco FTDv configured in routed mode and managed by a physical FMC appliance on-premises
D. Cisco FTDv with two management interfaces and one traffic interface configured
E. Cisco FTDv configured in routed mode and IPv6 configured
Correct Answer: AC
Reference: https://www.cisco.com/c/en/us/products/collateral/security/adaptive-security-virtual-appliance-asav/whitepaper-c11-740505.html
QUESTION 10
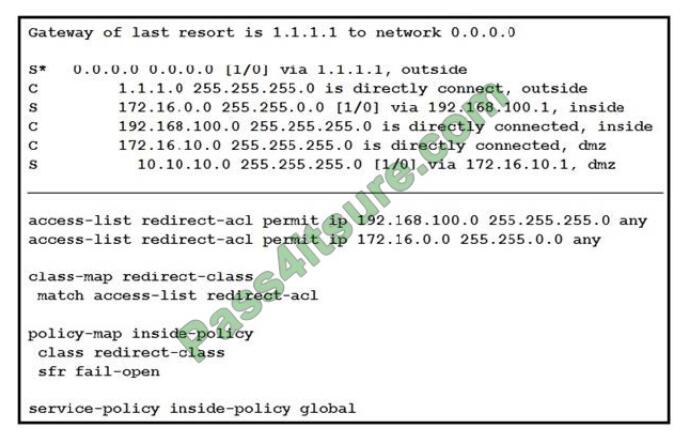
Refer to the exhibit. What is the result of the configuration?
A. Traffic from the DMZ network is redirected.
B. Traffic from the inside network is redirected.
C. All TCP traffic is redirected.
D. Traffic from the inside and DMZ networks is redirected.
Correct Answer: D
QUESTION 11
Which information is required when adding a device to Firepower Management Center?
A. username and password
B. encryption method
C. device serial number
D. registration key
Correct Answer: D
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmc-config-guidev60/Device_Management_Basics.html#ID-2242-0000069d
QUESTION 12
A sneaky employee using an Android phone on your network has disabled DHCP, enabled it\\’s firewall, modified it\\’s
HTTP User-Agent header, to tool ISE into profiling it as a Windows 10 machine connected to the wireless network. This
user
is now able to get authorization for unrestricted network access using his Active Directory credentials, as your policy
states that a Windows device using AD credentials should be able to get full network access. Whereas, an Android
device
should only get access to the Web proxy.
Which two steps can you take to avoid this sort of rogue behavior? (Choose two)
A. Create an authentication rule that should only allow session with a specific HTTP User-Agent header
B. Modify the authorization policy to only allow Windows machines that have passed Machine Authentication to get full
network access
C. Add an authorization policy before the Windows authorization policy that redirects a user with a static IP to a web
portal for authentication
D. Chain an authorization policy to the Windows authorization policy that performs additional NMAP scans to verify the
machine type, before allowing access
E. Only allow certificate-based authentication from Windows endpoints, such as EAP-TLS or PEAP- TLS. Should the
endpoint use MSCHAPv2 (EAP or PEAP), the user should be only given restricted access
F. Perform CoA to push restricted access when the machine is acquiring address using DHCP
Correct Answer: BE
QUESTION 13
Which feature requires a network discovery policy on the Cisco Firepower Next-Generation Intrusion Prevention
System?
A. security intelligence
B. impact flags
C. health monitoring
D. URL filtering
Correct Answer: A
Pass4itsure Discount Code 2020

P.S
Exampass shares all the resources: Latest Cisco 350-701 practice questions, latest 350-701 pdf dumps, 350-701 exam video learning. Cisco 350-701 dumps https://www.pass4itsure.com/350-701.html has come to help you prepare for the implementation of the Cisco 350-701 exam and its comprehensive and thorough 350-701 exam practice materials, which will help you successfully pass the examination.
Related
Discover more from Exampass: Collection of Cisco (CCNA, CCNP, Meraki Solutions Specialist, CCDP...) exam questions and answers from Pass4itsure
Subscribe to get the latest posts sent to your email.
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

