Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
Pass4itsure share these resources with you. Both VCE and PDF dumps contain the latest CompTIA CAS-003 exam questions, which will ensure your CAS-003 exam 100% passed! You can get CAS-003 VCE dumps and CAS-003 PDF dumps from Pass4itsure. Please get the latest Pass4itsure CAS-003 dumps here: https://www.pass4itsure.com/cas-003.html (553 QA Dumps).
Download The Real CompTIA CAS-003 PDF Here, Free
[free pdf] CompTIA CAS-003 PDF [Drive] https://drive.google.com/file/d/1ZHinRNC3Nhh9hVr8X8iuOqFMrwBoFipk/view?usp=sharing
CompTIA CAS-003 Practice Test Questions Answers
QUESTION 1
A malware infection spread to numerous workstations within the marketing department. The workstations were
quarantined and replaced with machines. Which of the following represents a FINAL step in the prediction of the
malware?
A. The workstations should be isolated from the network.
B. The workstations should be donated to refuse.
C. The workstations should be reimaged
D. The workstations should be patched and scanned.
Correct Answer: C
QUESTION 2
Joe, a penetration tester, is assessing the security of an application binary provided to him by his client. Which of the
The following methods would be the MOST effective in reaching this objective?
A. Employ a fuzzing utility
B. Use a static code analyzer
C. Run the binary in an application sandbox
D. Manually review the binary in a text editor
Correct Answer: C
QUESTION 3
A systems security engineer is assisting an organization\\’s market survey team in reviewing requirements for an
upcoming acquisition of mobile devices. The engineer expresses concerns to the survey team about a particular class of
devices that uses a separate SoC for baseband radio I/O. For which of the following reasons is the engineer
concerned?
A. These devices can communicate over networks older than HSPA+ and LTE standards, exposing device
communications to poor encryptions routines
B. The organization will be unable to restrict the use of NFC, electromagnetic induction, and Bluetooth technologies
C. The associated firmware is more likely to remain out of date and potentially vulnerable
D. The manufacturers of the baseband radios are unable to enforce mandatory access controls within their driver set
Correct Answer: B
QUESTION 4
After a security incident, an administrator would like to implement policies that would help reduce fraud and the potential
for collusion between employees. Which of the following would help meet these goals by having co-workers
occasionally audit another worker\\’s position?
A. Least privilege
B. Job rotation
C. Mandatory vacation
D. Separation of duties
Correct Answer: B
Job rotation can reduce fraud or misuse by preventing an individual from having too much control over an area.
QUESTION 5
A security firm is writing a response to an RFP from a customer that is building a new network-based software product.
The firm\\’s expertise is in penetration testing corporate networks. The RFP explicitly calls for all possible behaviors of
the product to be tested, however, it does not specify any particular method to achieve this goal. Which of the following
should be used to ensure the security and functionality of the product? (Select TWO).
A. Code review
B. Penetration testing
C. Grey box testing
D. Code signing
E. White box testing
Correct Answer: AE
A Code review refers to the examination of an application (the new network-based software product in this case) that is
designed to identify and assess threats to the organization.
White box testing assumes that the penetration test team has full knowledge of the network and the infrastructure per se
thus rendering the testing to follow a more structured approach.
QUESTION 6
A security consultant is considering authentication options for a financial institution. The following authentication options
are available security mechanisms to the appropriate use case. Options may be used once.
Select and Place:

QUESTION 7
A completely new class of web-based vulnerabilities has been discovered. Claims have been made that all common
web-based development frameworks are susceptible to attack. Proof-of-concept details have emerged on the Internet. A
security advisor within a company has been asked to provide recommendations on how to respond quickly to these
vulnerabilities. Which of the following BEST describes how the security advisor should respond?
A. Assess the reliability of the information source, likelihood of exploitability, and impact to hosted data. Attempt to
exploit via the proof-of-concept code. Consider remediation options.
B. Hire an independent security consulting agency to perform a penetration test of the web servers. Advise
management of any `high\\’ or `critical\\’ penetration test findings and put forward recommendations for mitigation.
C. Review vulnerability write-ups posted on the Internet. Respond to management with a recommendation to wait until
the news has been independently verified by software vendors providing the web application software.
D. Notify all customers about the threat to their hosted data. Bring the web servers down into “maintenance mode” until
the vulnerability can be reliably mitigated through a vendor patch.
Correct Answer: A
The first thing you should do is verify the reliability of the claims. From there you can assess the likelihood of the
vulnerability affecting your systems. If it is determined that your systems are likely to be affected by the exploit, you
need to determine what impact an attack will have on your hosted data. Now that you know what the impact will be, you
can test the exploit by using the proof-of-concept code. That should help you determine your options for dealing with the
threat (remediation).
QUESTION 8
A cybersecurity analyst is hired to review the security the posture of a company. The cybersecurity analyst notice a very
high network bandwidth consumption due to SYN floods from a small number of IP addresses. Which of the following
would be the BEST action to take to support incident response?
A. Increase the company\\’s bandwidth.
B. Apply ingress filters at the routers.
C. Install a packet capturing tool.
D. Block all SYN packets.
Correct Answer: B
QUESTION 9
While conducting a BIA for a proposed acquisition, the IT integration team found that both companies outsource CRM
services to competing and incompatible third-party cloud services. The decision has been made to bring the CRM
service in-house, and the IT team has chosen a future solution. With which of the following should the Chief Information
Security Officer (CISO) be MOST concerned? (Choose two.)
A. Data remnants
B. Sovereignty
C. Compatible services
D. Storage encryption
E. Data migration
F. Chain of custody
Correct Answer: CE
QUESTION 10
A security assessor is working with an organization to review the policies and procedures associated with managing the
organization\\’s virtual infrastructure. During a review of the virtual environment, the assessor determines the
organization is using servers to provide more than one primary function, which violates a regulatory requirement. The
assessor reviews hardening guides and determine policy allows for this configuration. It would be MOST appropriate
for the assessor to advise the organization to:
A. segment dual-purpose systems on a hardened network segment with no external access
B. assess the risks associated with accepting non-compliance with regulatory requirements
C. update system implementation procedures to comply with regulations
D. review regulatory requirements and implement new policies on any newly provisioned servers
Correct Answer: A
QUESTION 11
A security analyst works for a defense contractor that produces classified research on drones. The contractor’s faces
nearly constant attacks from sophisticated nation-state actors and other APIs.
Which of the following would help protect the confidentiality of the research data?
A. Use diverse components in layers throughout the architecture
B. Implement non-heterogeneous components at the network perimeter
C. Purge all data remnants from client devices\\’ volatile memory at regularly scheduled intervals
D. Use only in-house developed applications that adhere to strict SDLC security requirements
Correct Answer: A
QUESTION 12
The finance department for an online shopping website has discovered that a number of customers were able to
purchase goods and services without any payments. Further analysis conducted by the security investigations team
indicated that the website allowed customers to update a payment amount for shipping. A specially crafted value could
be entered and cause a rollover, resulting in the shipping cost being subtracted from the balance and in some instances
resulted in a negative balance. As a result, the system processed the negative balance as zero dollars. Which of the
following BEST describes the application issue?
A. Race condition
B. Click-jacking
C. Integer overflow
D. Use after free
E. SQL injection
Correct Answer: C
Integer overflow errors can occur when a program fails to account for the fact that an arithmetic operation can result in a
quantity either greater than a data type\\’s maximum value or less than its minimum value.
QUESTION 13
An information security officer is responsible for one secure network and one office network. Recent intelligence
suggests there is an opportunity for attackers to gain access to the secure network due to similar login credentials
across networks. To determine the users who should change their information, the information security officer uses a
tool to scan a file with hashed values on both networks and receives the following data:
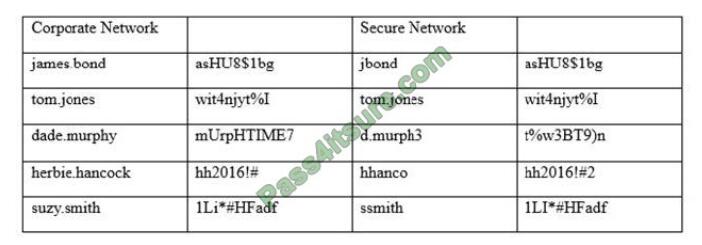
Which of the following tools was used to gather this information from the hashed values in the file?
A. Vulnerability scanner
B. Fuzzer
C. MD5 generator
D. Password cracker
E. Protocol analyzer
Correct Answer: C
Pass4itsure Discount Code 2020

P.S
Exampass shares all the resources: Latest CompTIA CAS-003 practice questions, latest CAS-003 pdf dumps, CAS-003 exam video learning. CompTIA CAS-003 dumps https://www.pass4itsure.com/cas-003.html has come to help you prepare for the implementation of the CompTIA CAS-003 exam and its comprehensive and thorough CAS-003 exam practice materials, which will help you successfully pass the examination.
Related
Discover more from Exampass: Collection of Cisco (CCNA, CCNP, Meraki Solutions Specialist, CCDP...) exam questions and answers from Pass4itsure
Subscribe to get the latest posts sent to your email.
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

