Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
Pass4itsure share these resources with you. Both VCE and PDF dumps contain the latest CompTIA CS0-002 exam questions, which will ensure your CS0-002 exam 100% passed! You can get CS0-002 VCE dumps and CS0-002 PDF dumps from Pass4itsure. Please get the latest Pass4itsure CS0-002 dumps here: https://www.pass4itsure.com/cs0-002.html (119 QA Dumps).
Download The Real CompTIA CS0-002 PDF Here, Free
[free pdf] CompTIA CS0-002 PDF [Drive] https://drive.google.com/file/d/1CCNdcXiubvCtUwMK04DfZwfE70d4m3_p/view?usp=sharing
CompTIA CS0-002 Practice Test Questions Answers
QUESTION 1
A security analyst is providing a risk assessment for a medical device that will be installed on the corporate network.
During the assessment, the analyst discovers the device has an embedded operating system that will be at the end of
its life in two years. Due to the criticality of the device, the security committee makes a risk-based policy decision to
review and enforce the vendor upgrade before the end of life is reached.
Which of the following risk actions has the security committee taken?
A. Risk exception
B. Risk avoidance
C. Risk tolerance
D. Risk acceptance
Correct Answer: D
QUESTION 2
A Chief Information Security Officer (CISO) wants to upgrade an organization\\’s security posture by improving proactive
activities associated with attacks from internal and external threats.
Which of the following is the MOST proactive tool or technique that feeds incident response capabilities?
A. Development of a hypothesis as part of threat hunting
B. Log correlation, monitoring, and automated reporting through a SIEM platform
C. Continuous compliance monitoring using SCAP dashboards
D. Quarterly vulnerability scanning using credentialed scans
Correct Answer: A
QUESTION 3
A security analyst is reviewing vulnerability scan results and notices new workstations are being flagged as having
outdated antivirus signatures. The analyst observes the following plugin output:
Antivirus is installed on the remote host:
Installation path: C:\Program Files\AVProduct\Win32\
Product Engine: 14.12.101
Engine Version: 3.5.71
Scanner does not currently have information about AVProduct version 3.5.71. It may no longer be supported.
The engine version is out of date. The oldest supported version from the vendor is 4.2.11.
The analyst uses the vendor\\’s website to confirm the oldest supported version is correct.
Which of the following BEST describes the situation?
A. This is a false positive, and the scanning plugin needs to be updated by the vendor.
B. This is a true negative, and the new computers have the correct version of the software.
C. This is a true positive, and the new computers were imaged with an old version of the software.
D. This is a false negative, and the new computers need to be updated by the desktop team.
Correct Answer: D
QUESTION 4
Ransomware is identified on a company\\’s network that affects both Windows and MAC hosts. The command and
control channel for encryption for this variant uses TCP ports from 11000 to 65000. The channel goes to good1.
Iholdbadkeys.com, which resolves to IP address 72.172.16.2.
Which of the following is the MOST effective way to prevent any newly infected systems from actually encrypting the
data on connected network drives while causing the least disruption to normal Internet traffic?
A. Block all outbound traffic to web host good1 iholdbadkeys.com at the border gateway.
B. Block all outbound TCP connections to IP host address 172.172.16.2 at the border gateway.
C. Block all outbound traffic on TCP ports 11000 to 65000 at the border gateway.
D. Block all outbound traffic on TCP ports 11000 to 65000 to IP host address 172.172.16.2 at the border gateway.
Correct Answer: A
QUESTION 5
For machine learning to be applied effectively toward security analysis automation, it requires __________.
A. relevant training data.
B. a threat feed API.
C. a multicore, multiprocessor system.
D. anomalous traffic signatures.
Correct Answer: D
QUESTION 6
An information security analyst observes anomalous behavior on the SCADA devices in a power plant. This behavior
results in the industrial generators overheating and destabilizing the power supply. Which of the following would BEST
identify potential indicators of compromise?
A. Use Burp Suite to capture packets to the SCADA device\\’s IP.
B. Use tcpdump to capture packets from the SCADA device IP.
C. Use Wireshark to capture packets between SCADA devices and the management system.
D. Use Nmap to capture packets from the management system to the SCADA devices.
Correct Answer: C
QUESTION 7
A security analyst receives an alert that highly sensitive information has left the company\\’s network Upon investigation,
the analyst discovers an outside IP range has had connections from three servers more than 100 times m the past
month The affected servers are virtual machines Which of the following is the BEST course of action?
A. Shut down the servers as soon as possible, move them to a clean environment, restart, run a vulnerability scanner to
find weaknesses determine the root cause, remediate, and report
B. Report the data exfiltration to management take the affected servers offline, conduct an antivirus scan, remediate all
threats found, and return the servers to service.
C. Disconnect the affected servers from the network, use the virtual machine console to access the systems, determine
which information has left the network, find the security weakness, and remediate
D. Determine if any other servers have been affected, snapshot any servers found, determine the vector that was used
to allow the data exfiltration. fix any vulnerabilities, remediate, report.
Correct Answer: A
QUESTION 8
A security analyst needs to reduce the overall attack surface.
Which of the following infrastructure changes should the analyst recommend?
A. Implement a honeypot.
B. Air gap sensitive systems.
C. Increase the network segmentation.
D. Implement a cloud-based architecture.
Correct Answer: C
Reference: https://www.securitymagazine.com/articles/89283-ways-to-reduce-your-attack-surface
QUESTION 9
A security analyst is reviewing a web application. If an unauthenticated user tries to access a page in the application,
the user is redirected to the login page. After successful authentication, the user is then redirected back to the original
page. Some users have reported receiving phishing emails with a link that takes them to the application login page but
then redirects to a fake login page after successful authentication.
Which of the following will remediate this software vulnerability?
A. Enforce unique session IDs for the application.
B. Deploy a WAF in front of the web application.
C. Check for and enforce the proper domain for the redirect.
D. Use a parameterized query to check the credentials.
E. Implement email filtering with anti-phishing protection.
Correct Answer: A
QUESTION 10
A security analyst reviews the following aggregated output from an Nmap scan and the border firewall ACL:
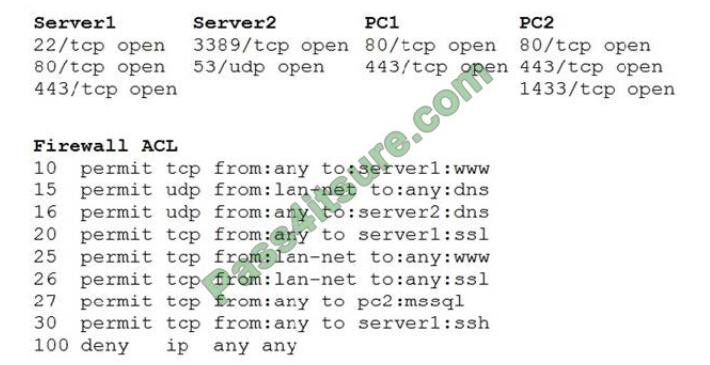
Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current
functionality?
A. PC1
B. PC2
C. Server1
D. Server2
E. Firewall
Correct Answer: E
QUESTION 11
A security analyst discovers accounts in sensitive SaaS-based systems are not being removed in a timely manner when
an employee leaves the organization To BEST resolve the issue, the organization should implement
A. federated authentication
B. role-based access control.
C. manual account reviews
D. multifactor authentication.
Correct Answer: A
QUESTION 12
SIMULATION
You are a cybersecurity analyst tasked with interpreting scan data from Company A\\’s servers. You must verify the
requirements are being met for all of the servers and recommend changes if you find they are not.
The company\\’s hardening guidelines indicate the following:
1.
TLS 1.2 is the only version of TLS running.
2.
Apache 2.4.18 or greater should be used.
3.
Only default ports should be used.
INSTRUCTIONS
Using the supplied data, record the status of compliance with the company\\’s guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for issues based
ONLY on the hardening guidelines provided.
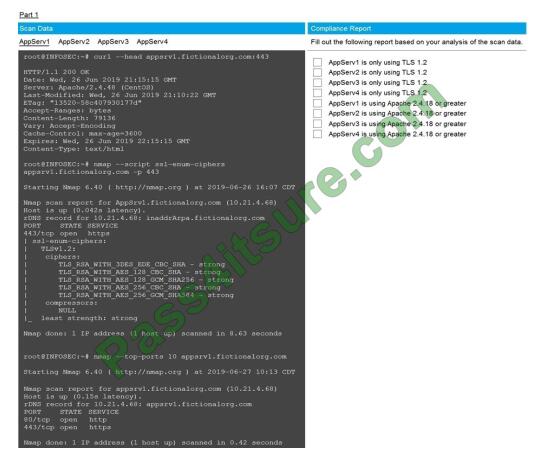
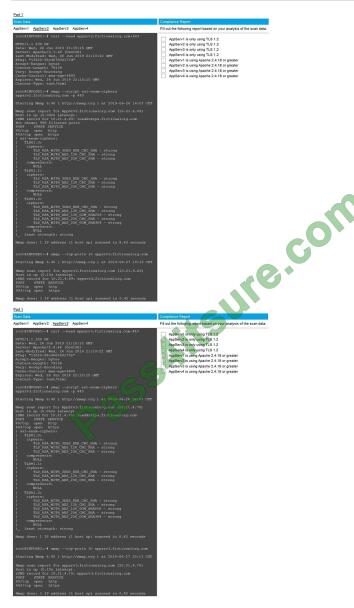
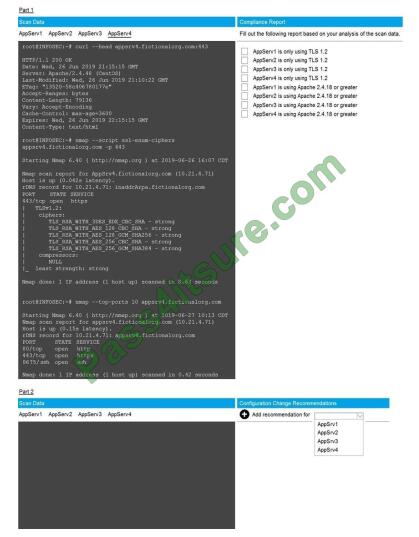
A.
Correct Answer: See below.
QUESTION 13
Which of the following roles is ultimately responsible for determining the classification levels assigned to specific data
sets?
A. Data custodian
B. Data owner
C. Data processor
D. Senior management
Correct Answer: B
Reference: https://www.pearsonitcertification.com/articles/article.aspx?p=2731933andseqNum=3
Pass4itsure Discount Code 2020

P.S
Exampass shares all the resources: Latest CompTIA CS0-002 practice questions, latest CS0-002 pdf dumps, CS0-002 exam video learning. CompTIA CS0-002 dumps https://www.pass4itsure.com/cs0-002.html has come to help you prepare for the implementation of the CompTIA CS0-002 exam and its comprehensive and thorough CS0-002 exam practice materials, which will help you successfully pass the examination.
Related
Discover more from Exampass: Collection of Cisco (CCNA, CCNP, Meraki Solutions Specialist, CCDP...) exam questions and answers from Pass4itsure
Subscribe to get the latest posts sent to your email.
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

