Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)

How to Prepare for Performing CyberOps Using Cisco Security Technologies 350-201 Exam? This article will tell you how to prepare for the 350-201 exam, the steps to prepare, and the latest 350-201 exam practice questions to share.
It tells you how to prepare for the 350-201 exam
First, you must be clear: preparing for the Cisco (Performing CyberOps Using Cisco Security Technologies) 350-201 exam requires clear steps and a lot of patience.
Let’s start with the steps to prepare for the exam
Preparing for the Cisco 350-201 exam is a careful job, you need clear steps, step by step, in a hurry:
The first step is to understand the exam blueprint provided by Cisco.
| Exam Title: | Performing Network Operations Using Cisco Security Technologies |
| Exam Code: | 350-201 CBRCOR |
| Exam Price: | $400 |
| Duration: | 120 minutes |
| Several questions: | 90-110 |
| Passing Score: | Variable (750-850 / 1000 approx.) |
| After passing the exam: | Earn a network operations associate and also, after the exam, review your performance and use the experience to guide further learning and professional development. |
| Exam topics: Fundamentals – 20%, Technology – 30%, Process – 30%, Automation – 20% | Fundamentals – 20%, Technology – 30%, Process – 30%, Automation – 20% |
| 350-201 Exam Objectives: | Test your foundational knowledge, skills, processes, automation, knowledge, and skills related to core cybersecurity operations Network Operations Assistant |
| What you need to take the test: | A government-issued photo ID and the candidate’s signature are required |
The second step is to gather study materials, including official guides, online courses, books, and practice exams, among others.
You can find the best learning materials on the Cisco.com, Cisco Learning Network, and Pearson VUE websites. Of course, there are others.
Useful Resource Links for Studying for the 350-201 CBRCOR Exam:
https://www.netacad.com/courses/cybersecurity/cyberops-associate
https://learningnetworkstore.cisco.com/on-demand-e-learning/performing-cyberops-using-cisco-security-technologies-cbrcor-v1.0/CSCU-LP-CBRCOR-V1-028091.html
https://zcybersecurity.com/nist-incident-response-plan-playbook/
https://cybersecurity.att.com/resource-center/ebook/insider-guide-to-incident-response/incident-response-process-and-procedures
https://learningnetwork.cisco.com/s/cyberops-professional
The third step is to practice and practice the exam questions and test the learning results.
If you want a free practice exam for the 350-201, you can download the PDF free demo directly on Pass4itSure. Free practice exam questions (350-201 exam practice questions) are also available here.
The latest 350-201 exam practice questions are shared online
Question 1:
An engineer notices that every Sunday night, there is a two-hour period with a large load of network activity. Upon further investigation, the engineer finds that the activity is from locations around the globe outside the organization\’s service area. What are the next steps the engineer must take?
A. Assign the issue to the incident handling provider because no suspicious activity has been observed during business hours.
B. Review the SIEM and FirePower logs, block all traffic, and document the results of calling the call center.
C. Define the access points using StealthWatch or SIEM logs, understand services being offered during the hours in question, and cross-correlate other source events.
D. Treat it as a false positive, and accept the SIEM issue as valid to avoid alerts from triggering on weekends.
Correct Answer: A
Question 2:
A security expert is investigating a breach that resulted in a $32 million loss from customer accounts. Hackers were able to steal API keys and two-factor codes due to a vulnerability that was introduced in a new code a few weeks before the attack.
Which step was missed that would have prevented this breach?
A. use of the Nmap tool to identify the vulnerability when the new code was deployed
B. implementation of a firewall and intrusion detection system
C. implementation of an endpoint protection system
D. use of SecDevOps to detect the vulnerability during development
Correct Answer: D
Reference: https://securityintelligence.com/how-to-prioritize-security-vulnerabilities-in-secdevops/
Question 3:
An engineer has created a bash script to automate a complicated process. During script execution, this error occurs permission denied. Which command must be added to execute this script?
A. chmod +x ex. sh
B. source ex. sh
C. chroot ex. sh
D. sh ex. sh
Correct Answer: A
Reference: https://www.redhat.com/sysadmin/exit-codes-demystified
Question 4:
A threat actor attacked an organization\’s Active Directory server from a remote location, and in a thirty-minute timeframe, stole the password for the administrator account and attempted to access 3 company servers. The threat actor successfully accessed the first server that contained sales data, but no files were downloaded. A second server was also accessed that contained marketing information and 11 files were downloaded. When the threat actor accessed the third server that contained corporate financial data, the session was disconnected, and the administrator\’s account was disabled.
Which activity triggered the behavior analytics tool?
A. accessing the Active Directory server
B. accessing the server with financial data
C. accessing multiple servers
D. downloading more than 10 files
Correct Answer: C
Question 5:
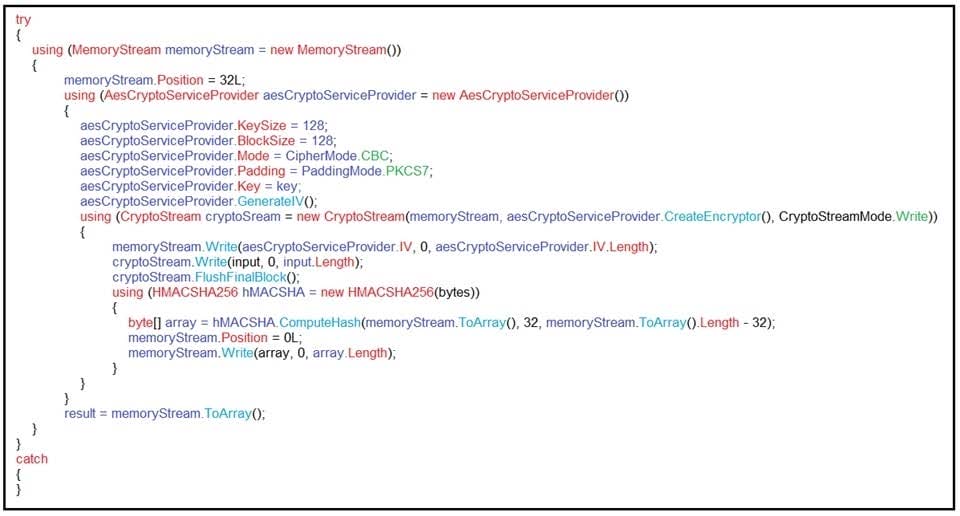
Refer to the exhibit. An engineer is performing a static analysis on malware and knows that it is capturing keys and webcam events on a company server. What is the indicator of compromise?
A. The malware is performing comprehensive fingerprinting of the host, including a processor, motherboard manufacturer, and connected removable storage.
B. The malware is ransomware querying for installed anti-virus products and operating systems to encrypt and render unreadable until payment is made for file decryption.
C. The malware has moved to harvesting cookies and stored account information from major browsers and configuring a reverse proxy for intercepting network activity.
D. The malware contains an encryption and decryption routine to hide URLs/IP addresses and is storing the output of loggers and webcam captures in locally encrypted files for retrieval.
Correct Answer: B
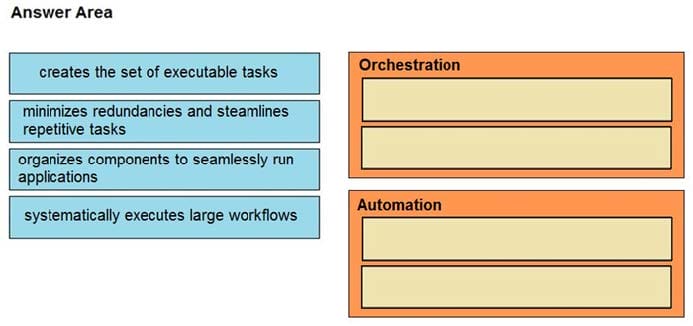
Question 6:
DRAG DROP
Drag and drop the function on the left onto the mechanism on the right.
Select and Place:
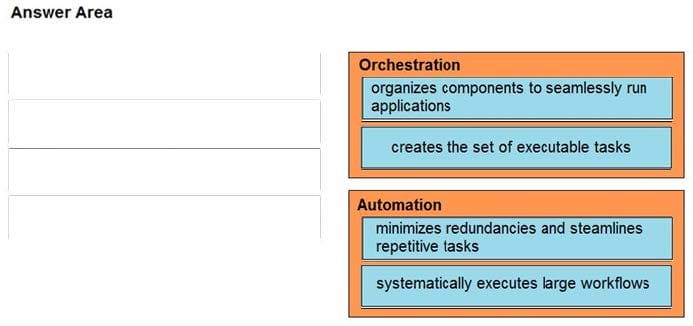
Correct Answer:
Question 7:
Refer to the exhibit. Based on the detected vulnerabilities, what is the next recommended mitigation step?
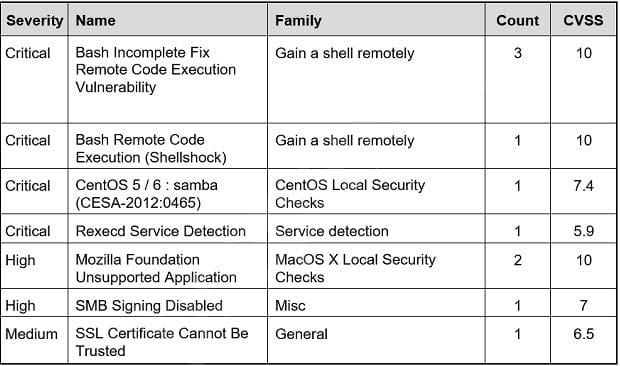
A. Evaluate service disruption and associated risk before prioritizing patches.
B. Perform root cause analysis for all detected vulnerabilities.
C. Remediate all vulnerabilities with descending CVSS score order.
D. Temporarily shut down unnecessary services until patch deployment ends.
Correct Answer: B
Question 8:
A SOC team is investigating a recent, targeted social engineering attack on multiple employees. Cross-correlated log analysis revealed that two hours before the attack, multiple assets received requests on TCP port 79. Which action should be taken by the SOC team to mitigate this attack?
A. Disable BIND forwarding from the DNS server to avoid reconnaissance.
B. Disable affected assets and isolate them for further investigation.
C. Configure affected devices to disable NETRJS protocol.
D. Configure affected devices to disable the Finger service.
Correct Answer: D
Question 9:
A payroll administrator noticed unexpected changes within a piece of software and reported the incident to the incident response team. Which actions should be taken at this step in the incident response workflow?
A. Classify the criticality of the information, research the attacker\’s motives, and identify missing patches
B. Determine the damage to the business, extract reports, and save evidence according to a chain of custody
C. Classify the attack vector, understand the scope of the event, and identify the vulnerabilities being exploited
D. Determine the attack surface, evaluate the risks involved, and communicate the incident according to the escalation plan
Correct Answer: B
Question 10:
A security manager received an email from an anomaly detection service, that one of their contractors has downloaded 50 documents from the company\’s confidential document management folder using a company-owned asset al039-ice4ce687TL0500. A security manager reviewed the content of downloaded documents and noticed that the data affected was from different departments. What are the actions a security manager should take?
A. Measure the confidentiality level of downloaded documents.
B. Report to the incident response team.
C. Escalate to the contractor\’s manager.
D. Communicate with the contractor to identify the motives.
Correct Answer: B
Question 11:
A SOC team receives multiple alerts by a rule that detects requests to malicious URLs and informs the incident response team to block the malicious URLs requested on the firewall. Which action will improve the effectiveness of the process?
A. Block local to remote HTTP/HTTPS requests on the firewall for users who triggered the rule.
B. Inform the user by enabling an automated email response when the rule is triggered.
C. Inform the incident response team by enabling an automated email response when the rule is triggered.
D. Create an automation script for blocking URLs on the firewall when the rule is triggered.
Correct Answer: A
Question 12:
An engineer is investigating several cases of increased incoming spam emails and suspicious emails from the HR and service departments. While checking the event sources, the website monitoring tool showed several web scraping alerts overnight.
Which type of compromise is indicated?
A. phishing
B. dumpster diving
C. social engineering
D. privilege escalation
Correct Answer: C
Question 13:
Refer to the exhibit. Where is the MIME type that should be followed indicated?
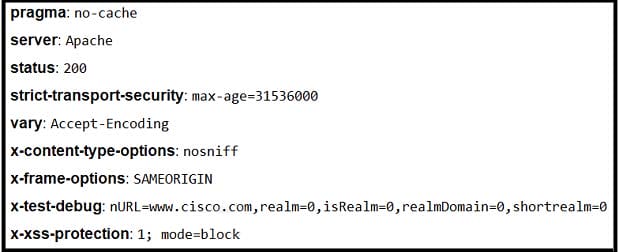
A. x-test-debug
B. strict-transport-security
C. x-xss-protection
D. x-content-type-options
Correct Answer: A
Question 14:
What is the benefit of key risk indicators?
A. clear perspective into the risk position of an organization
B. improved visibility on quantifiable information
C. improved mitigation techniques for unknown threats
D. clear procedures and processes for organizational risk
Correct Answer: C
Question 15:
An engineer receives an incident ticket with hundreds of intrusion alerts that require investigation. An analysis of the incident log shows that the alerts are from trusted IP addresses and internal devices. The final incident report stated that these alerts were false positives and that no intrusions were detected.
What action should be taken to harden the network?
A. Move the IPS to after the firewall facing the internal network
B. Move the IPS to before the firewall facing the outside network
C. Configure the proxy service on the IPS
D. Configure reverse port forwarding on the IPS
Correct Answer: C
Check out the last updated 350-201 exam questions here.
Pass4itSure offers 350-201 practice exam questions in PDF and VCE formats with 139+. These questions will help you better prepare for the Cisco CyberOps Professional certification.
Step 4: Join study groups and forums to collaborate with others to learn more and review regularly.
Join an online forum, study group, or community dedicated to your Cisco CyberOps certification. Communicate study materials, share tips, and discuss exam-related topics with other test takers.
Step 5: Schedule your exam through the Pearson VUE website
Please note that you will need your ID and signature in advance to register for the exam. The rest will come as requested.
By following these steps and focusing on your studies, you will be well-prepared to pass the CBR-COR 350-201 exam and earn the Cisco Certified CyberOps Professional certification.
More than 255,199 network operations assistants have been registered
More than 255,199 people have registered as network operations assistants, and the news comes from Cisco. This data shows that the popularity of this position also proves that it is necessary to pass the 350-201 exam. This is of great benefit to your employment.
And also…
There are 9,058 vacancies for Network Operations Assistants on Indeed.com.
Ziprecruiter.com 47,171 Global Network Operations positions ($93k-$161k) that are being hired.
You haven’t come to study for the 350-201 exams yet?
Career pathways after passing the Cisco 350-201 exam:
Because 350-201 focuses on your knowledge and skills related to core cybersecurity operations, it can be found in the following roles:
Securities analyst: Analyze and interpret security data to enhance an organization’s overall security posture.
Incident responders: Individuals can respond quickly and effectively to security incidents, mitigate potential damage, and ensure a quick return to normal.
Cybersecurity Officer: Designs and implements robust cybersecurity measures.
Network Operations Associate: Develop monitoring, detecting, and responding to cybersecurity threats.
Summary:
Ready to start your Cisco 350-201 exam?
Pass4itSure 350-201 exam practice questions https://www.pass4itsure.com/350-201.html are highly recommended to ensure that you are always up-to-date with the latest cybersecurity technology, which can help you study for the exam with ease. With tips on how to prepare for the 350-201 exam, prepare for the exam steps, the job opportunities, and more, you’ll be ready to take the 350-201 CBRCOR exam and get certified to start your career in cybersecurity!
Related
Discover more from Exampass: Collection of Cisco (CCNA, CCNP, Meraki Solutions Specialist, CCDP...) exam questions and answers from Pass4itsure
Subscribe to get the latest posts sent to your email.
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

