Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)

Choosing the Cisco certification CyberOps Professional exam opens the door to better job opportunities. Undoubtedly, preparing for this exam is a daunting task. What do you do? Are you scared of exams?
Let us help you: This article debunks the dreaded myth of passing the Cisco CyberOps Professional exam and shares the latest 300-215 and 350-201 exam practice questions online. Using these tips, you can earn the Cisco CyberOps Professional certification.
What you need to know about Cisco CyberOps Professional
Cisco certification CyberOps Professional: Demonstrate your expertise in preventing cyberattacks, responding to incidents, and securing the cloud with the CyberOps Professional certification. Having this certification demonstrates that you can reliably identify and respond to cybersecurity threats and incidents. Become one of the biggest assets in one of the most in-demand areas for IT.
The above is taken from: https://www.cisco.com/site/us/en/learn/training-certifications/certifications/cyberops/cyberops-professional/index.html
The Cisco CyberOps Professional consists of three exams: Core Exams
350-201 CBRCOR v1.1, 300-215 CBRFIR v1.1 or 300-220 CBRTHD v1.0.
Among them, the core exam 350-201 CBRCOR v1.1 is that you must pass, and you need to choose one of the two centralized exams to pass.
| Exam Objectives | Demonstrate your expertise in preventing cyberattacks, responding to incidents, and securing the cloud |
| Exam Structure | Cisco CyberOps Professional consists of two parts: the 350-201 CBRCOR (core exam) and the 300-215 CBRFIR or 300-220 CBRTHD (choose one of the centralized exams). Two exams must be passed to earn a certification. |
| Exam Validity | The certificate is valid for three years. |
| Exam Time | The core exam lasts 120 minutes and the concentration exam lasts 90 minutes, which are different in duration. |
| Exam location | It can be done online or in person. |
| Exam Fees | $400 for the Core Exam and $300 for the concentration exam can be redeemed for Cisco Learning Credits. |
| Exam Preparation | Involves official study materials, training courses, books, and mock exams. |
| Exam Topics | Core exams: Fundamentals 20%, Techniques 30%, Processes 30%, Automation 20%。Centralized exams 300-215:Fundamentals 20%,Forensics Techniques 20%,Incident Response Techniques 30%,Forensics Processes 15%,Incident Response Processes 15% Centralized exams 300-220:Threat Hunting Fundamentals 20%,Threat Modeling Techniques 10%,Threat Actor Attribution Techniques 20%,Threat Hunting Techniques 20%,Threat Hunting Processes 20%,Threat Hunting Outcomes 10% |
| The difference between the centralized examination 300-220 and 300-215 | 300-215 CBRFIR — Focused on forensic analysis and incident response, 300-220 CBRTHD — Focused on threat hunting and defense. |
Cisco Certified CyberOps Professional exam the right learning path
Step 1: Make sure it’s the right certificate for you
Step 2: Register for the exam
Step 3: Pass the 350-201 CBRCOR exam
Step 4: Pass 300-215 CBRFIR or 300-220 CBRTHD
How to choose the right centralized exam
Choose one of the two in the centralized exam, so the question is, how to choose the best, and what are the judging criteria?
My advice is that you should choose a focused exam based on your experience and level of interest in each exam.
Comparing these three points can help you:
Take a close look at the 300-215 CBRFIR and 300-220 CBRTHD exams and choose the one you are most likely to pass.
Study the two exam blueprints and choose the one that gives you the most confidence of the two.
Break down each topic of the exam, score it according to how easy it is to grasp the content, and use an analytical approach to make a decision.
In a nutshell, the Cisco 300-220 exam has slightly more areas, which means you may need a wider range of skills. However, for the Cisco 300-215 exam, you need to have slightly in-depth skills in each area as there are only five domains. It depends on your situation and experience. I’m just teaching you a line of thought for choosing.
How to study for the Cisco certification CyberOps Professional exam
The study of any exam is inseparable from the help of learning resources. There are no magic tricks other than focusing on your studies to ensure that you succeed in the CyberOps Professional exam. All you need to do is study hard. The following sections will focus on resources to help you prepare for the exam properly to achieve an excellent score and pass the exam.
- Make good use of books and study guides
This most traditional way of learning gives you a comprehensive understanding of the syllabus, topics, and content of the exam.
- Videos and official training courses
Videos are intuitive, a good learning resource, and they are also very popular. Official training courses are the best option to learn more about exam concepts.
- Join online communities and forums
Communities and forums are also great places to learn. Explore the answers to questions related to this Cisco exam in the community and forums and connect with other applicants.
- Take the CyberOps Professional exam practice test
Practice is the only criterion for testing truth, and the same is true for exams. Take the Cisco 300-215 CBRFIR practice tests, which can help you prepare for the real exam. Pass4itSure provides you with the CyberOps Professional exam 300-215 CBRFIR, 350-201 CBRCOR free practice test that you can explore online.
Up-to-date CyberOps Professional 350-201 CBRCOR Exam Practice Test
| From: | Includes exams: | Number of questions | Shape |
| Pass4itSure | Cisco 350-201 | 15 questions | Free |
Question 1:
The physical security department received a report that an unauthorized person followed an authorized individual to enter a secured premises. The incident was documented and given to a security specialist to analyze. Which step should be taken at this stage?
A. Determine the assets to which the attacker has access
B. Identify assets the attacker handled or acquired
C. Change access controls to high-risk assets in the enterprise
D. Identify the movement of the attacker in the enterprise
Correct Answer: D
Question 2:
A company\’s web server availability was breached by a DDoS attack and was offline for 3 hours because it was not deemed a critical asset in the incident response playbook. Leadership has requested a risk assessment of the asset. An analyst conducted the risk assessment using the threat sources, events, and vulnerabilities.
Which additional element is needed to calculate the risk?
A. assessment scope
B. event severity and likelihood
C. incident response playbook
D. risk model framework
Correct Answer: D
Question 3:
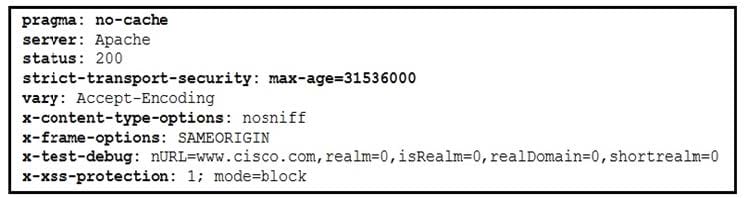
Refer to the exhibit. Where are the browser page rendering permissions displayed?
A. x-frame-options
B. x-xss-protection
C. x-content-type-options
D. x-test-debug
Correct Answer: C
Reference: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Content-Type-Options
Question 4:
An engineer is investigating several cases of increased incoming spam emails and suspicious emails from the HR and service departments. While checking the event sources, the website monitoring tool showed several web scraping alerts overnight.
Which type of compromise is indicated?
A. phishing
B. dumpster diving
C. social engineering
D. privilege escalation
Correct Answer: C
Question 5:
How is a SIEM tool used?
A. To collect security data from authentication failures and cyber-attacks and forward it for analysis
B. To search and compare security data against acceptance standards and generate reports for analysis
C. To compare security alerts against configured scenarios and trigger system responses
D. To collect and analyze security data from network devices and servers and produce alerts
Correct Answer: D
Reference: https://www.varonis.com/blog/what-is-siem/
Question 6:

Refer to the exhibit. IDS is producing an increased amount of false positive events about brute force attempts on the organization\’s mail server. How should the Snort rule be modified to improve performance?
A. Block list of internal IPs from the rule
B. Change the rule content match to case sensitive
C. Set the rule to track the source IP
D. Tune the count and seconds threshold of the rule
Correct Answer: B
Question 7:
A security engineer discovered that a spreadsheet containing confidential information for nine of their employees was fraudulently posted on a competitor\’s website. The spreadsheet contains names, salaries, and social security numbers. What is the next step the engineer should take in this investigation?
A. Determine if there is internal knowledge of this incident.
B. Check incoming and outgoing communications to identify spoofed emails.
C. Disconnect the network from Internet access to stop the phishing threats and regain control.
D. Engage the legal department to explore action against the competitor who posted the spreadsheet.
Correct Answer: D
Question 8:
A SOC team is investigating a recent, targeted social engineering attack on multiple employees. Cross-correlated log analysis revealed that two hours before the attack, multiple assets received requests on TCP port 79. Which action should be taken by the SOC team to mitigate this attack?
A. Disable BIND forwarding from the DNS server to avoid reconnaissance.
B. Disable affected assets and isolate them for further investigation.
C. Configure affected devices to disable NETRJS protocol.
D. Configure affected devices to disable the Finger service.
Correct Answer: D
Question 9:
An employee abused PowerShell commands and script interpreters, which led to an indicator of compromise (IOC) trigger. The IOC event shows that a known malicious file has been executed, and there is an increased likelihood of a breach.
Which indicator generated this IOC event?
A. ExecutedMalware.ioc
B. Crossrider. ioc
C. ConnectToSuspiciousDomain.ioc
D. W32 AccesschkUtility.ioc
Correct Answer: D
Question 10:
An engineer is utilizing interactive behavior analysis to test malware in a sandbox environment to see how the malware performs when it is successfully executed. A location is secured to perform reverse engineering on a piece of malware. What is the next step the engineer should take to analyze this malware?
A. Run the program through a debugger to see the sequential actions
B. Unpack the file in a sandbox to see how it reacts
C. Research the malware online to see if there are noted findings
D. Disassemble the malware to understand how it was constructed
Correct Answer: C
Question 11:
Refer to the exhibit. Based on the detected vulnerabilities, what is the next recommended mitigation step?
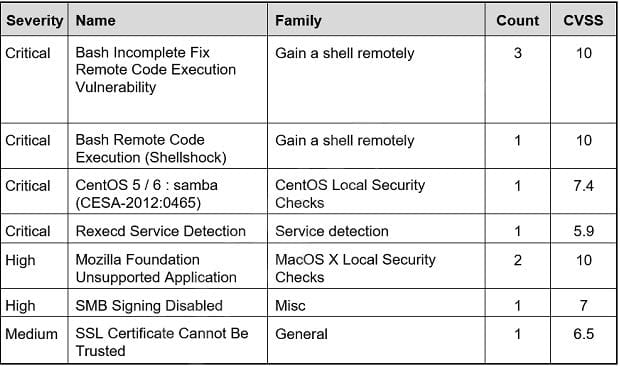
A. Evaluate service disruption and associated risk before prioritizing patches.
B. Perform root cause analysis for all detected vulnerabilities.
C. Remediate all vulnerabilities with descending CVSS score order.
D. Temporarily shut down unnecessary services until patch deployment ends.
Correct Answer: B
Question 12:
A SOC analyst is investigating a recent email delivered to a high-value user for a customer whose network their organization monitors. The email includes a suspicious attachment titled “Invoice RE: 0004489”. The hash of the file is gathered from the Cisco Email Security Appliance. After searching Open Source Intelligence, no available history of this hash is found anywhere on the web.
What is the next step in analyzing this attachment to allow the analyst to gather indicators of compromise?
A. Run and analyze the DLP Incident Summary Report from the Email Security Appliance
B. Ask the company to execute the payload for real-time analysis
C. Investigate further in open source repositories using YARA to find matches
D. Obtain a copy of the file for detonation in a sandbox
Correct Answer: D
Question 13:
An engineer is moving data from NAS servers in different departments to a combined storage database so that the data can be accessed and analyzed by the organization on demand. Which data management process is being used?
A. data clustering
B. data regression
C. data ingestion
D. data obfuscation
Correct Answer: A
Question 14:
A threat actor attacked an organization\’s Active Directory server from a remote location, and in a thirty-minute timeframe, stole the password for the administrator account and attempted to access 3 company servers. The threat actor successfully accessed the first server that contained sales data, but no files were downloaded. A second server was also accessed that contained marketing information and 11 files were downloaded. When the threat actor accessed the third server that contained corporate financial data, the session was disconnected, and the administrator\’s account was disabled.
Which activity triggered the behavior analytics tool?
A. accessing the Active Directory server
B. accessing the server with financial data
C. accessing multiple servers
D. downloading more than 10 files
Correct Answer: C
Question 15:
A logistic company must use an outdated application located in a private VLAN during the migration to new technologies. The IPS blocked and reported an unencrypted communication. Which tuning option should be applied to IPS?
A. Allow list only authorized hosts to contact the application\’s IP at a specific port.
B. Allow list HTTP traffic through the corporate VLANS.
C. Allow list traffic to application\’s IP from the internal network at a specific port.
D. Allow list only authorized hosts to contact the application\’s VLAN.
Correct Answer: D
Pass4itSure Cisco 350-201 Exam Practice Questions: 139 QAs https://www.pass4itsure.com/350-201.html
Up-to-date CyberOps Professional 300-215 Exam Practice Test
| From: | Includes exams: | Number of questions | Shape |
| Pass4itSure | Cisco 300-215 | 15 questions | Free |
Question 1:
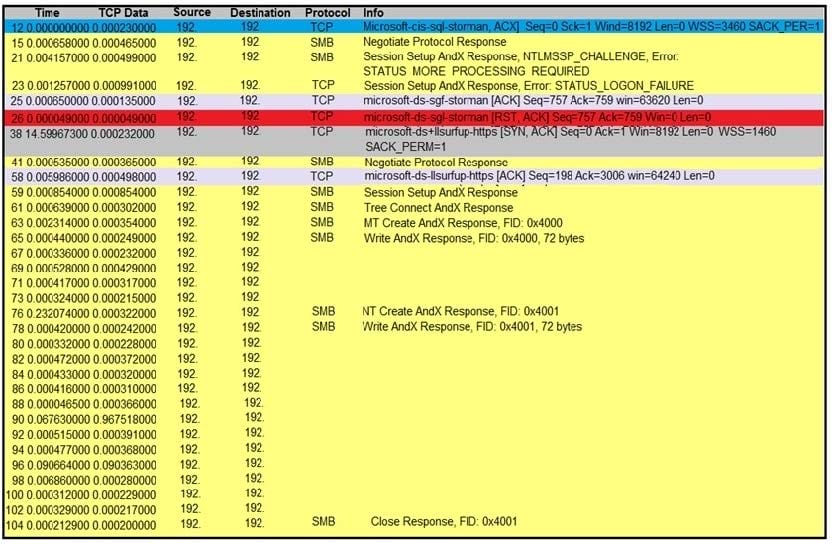
Refer to the exhibit. An engineer is analyzing a TCP stream in a Wireshark after a suspicious email with a URL. What should be determined about the SMB traffic from this stream?
A. It is redirecting to a malicious phishing website,
B. It is exploiting redirect vulnerability C. It is requesting authentication on the user site.
D. It is sharing access to files and printers.
Correct Answer: B
Question 2:
Which scripts will search a log file for the IP address of 192.168.100.100 and create an output file named parsed_host.log while printing results to the console?

A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: A
Question 3:
A website administrator has an output of an FTP session that runs nightly to download and unzip files to a local staging server. The download includes thousands of files, and the manual process used to find how many files failed to download is time-consuming. The administrator is working on a PowerShell script that will parse a log file and summarize how many files were successfully downloaded versus ones that failed. Which script will read the contents of the file one line at a time and return a collection of objects?
A. Get-Content-Folder \\Server\FTPFolder\Logfiles\ftpfiles.log | Show-From “ERROR”, “SUCCESS”
B. Get-Content –ifmatch \\Server\FTPFolder\Logfiles\ftpfiles.log | Copy-Marked “ERROR”, “SUCCESS”
C. Get-Content –Directory \\Server\FTPFolder\Logfiles\ftpfiles.log | Export-Result “ERROR”, “SUCCESS”
D. Get-Content –Path \\Server\FTPFolder\Logfiles\ftpfiles.log | Select-String “ERROR”, “SUCCESS”
Correct Answer: D
Question 4:
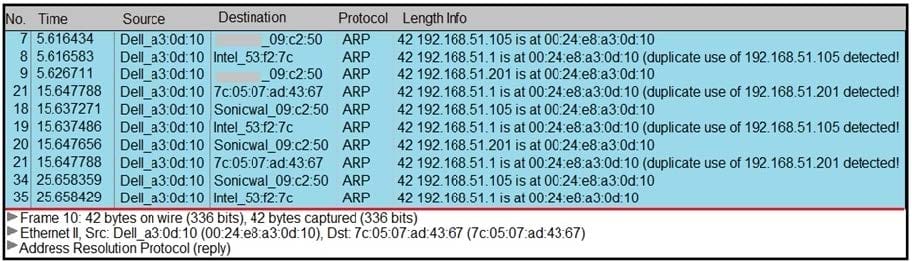
Refer to the exhibit. A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?
A. DNS spoofing; encrypt communication protocols
B. SYN flooding, block malicious packets
C. ARP spoofing; configure port security
D. MAC flooding; assign static entries
Correct Answer: C
Question 5:
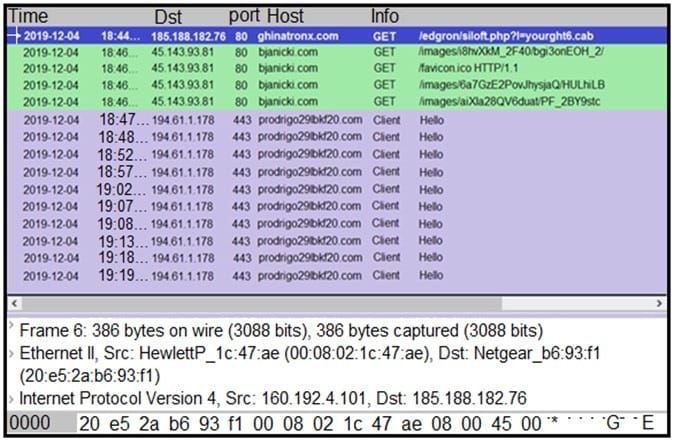
Refer to the exhibit. A network engineer is analyzing a Wireshark file to determine the HTTP request that caused the initial Ursnif banking Trojan binary to download. Which filter did the engineer apply to sort the Wireshark traffic logs?
A. http.request.un matches
B. tls.handshake.type ==1
C. tcp.port eq 25
D. tcp.window_size ==0
Correct Answer: B
Reference:
https://www.malware-traffic-analysis.net/2018/11/08/index.html
https://unit42.paloaltonetworks.com/wireshark-tutorial-examining-ursnif-infections
Question 6:
Over the last year, an organization\’s HR department has accessed data from its legal department on the last day of each month to create a monthly activity report. An engineer is analyzing suspicious activity alerted by a threat intelligence platform that an authorized user in the HR department has accessed legal data daily for the last week. The engineer pulled the network data from the legal department\’s shared folders and discovered above-average-size data dumps. Which threat actor is implied from these artifacts?
A. privilege escalation
B. internal user errors
C. malicious insider
D. external exfiltration
Correct Answer: C
Question 7:
An engineer is analyzing a ticket for an unexpected server shutdown and discovers that the web server ran out of usable memory and crashed.
Which data is needed for further investigation?
A. /var/log/access.log
B. /var/log/messages.log
C. /var/log/httpd/messages.log
D. /var/log/httpd/access.log
Correct Answer: B
Question 8:
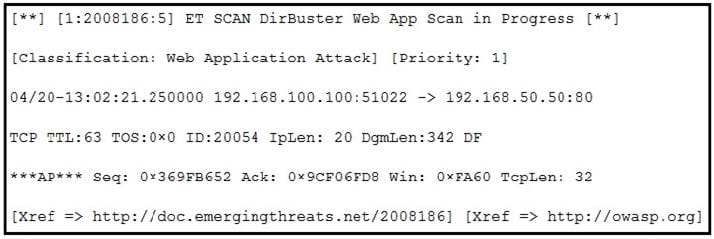
Refer to the exhibit. According to the SNORT alert, what is the attacker performing?
A. brute-force attack against the web application user accounts
B. XSS attack against the target web server
C. brute-force attack against directories and files on the target web server
D. SQL injection attack against the target web server
Correct Answer: C
Question 9:
An employee receives an email from a “trusted” person containing a hyperlink that is malvertising. The employee clicks the link and the malware downloads. An information analyst observes an alert at the SIEM and engages the cybersecurity team to conduct an analysis of this incident by the incident response plan. Which event detail should be included in this root cause analysis?
A. phishing email sent to the victim
B. alarm raised by the SIEM
C. information from the email header
D. alert identified by the cybersecurity team
Correct Answer: B
Question 10:
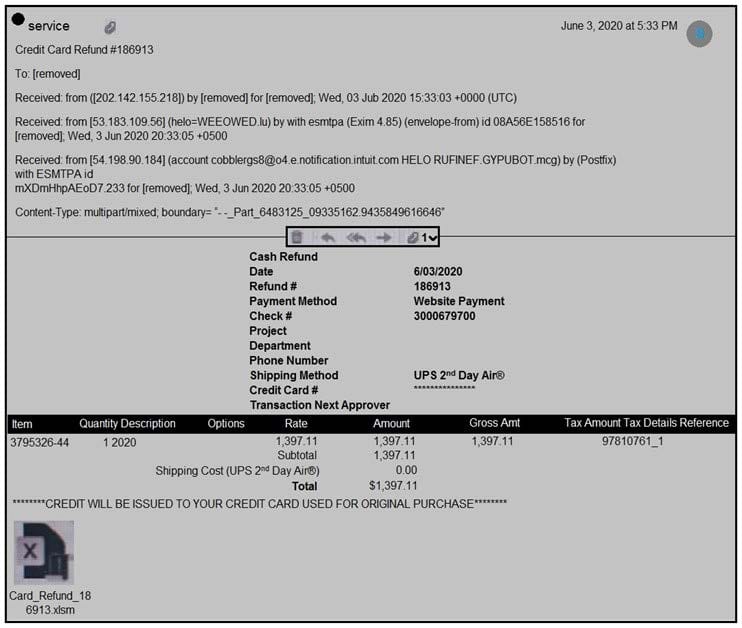
Refer to the exhibit. Which element in this email is an indicator of attack?
A. IP Address: 202.142.155.218
B. Content-Type: multipart/mixed
C. attachment: “Card-Refund”
D. subject: “Service Credit Card”
Correct Answer: C
Question 11:
An “unknown error code” is appearing on an ESXi host during authentication. An engineer checks the authentication logs but is unable to identify the issue. Analysis of the vCenter agent logs shows no connectivity errors. What is the next log file the engineer should check to continue troubleshooting this error?
A. /var/log/syslog.log
B. /var/log/vmksummary.log
C. var/log/shell.log
D. var/log/general/log
Correct Answer: A
Question 12:

Refer to the exhibit. Which type of code created the snippet?
A. VB Script
B. Python
C. PowerShell
D. Bash Script
Correct Answer: A
Question 13:
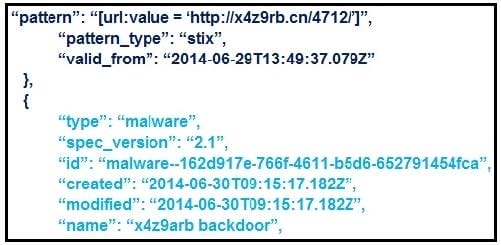
Refer to the exhibit. What is the IOC threat and URL in this STIX JSON snippet?
A. malware; `http://x4z9arb.cn/4712/\’
B. malware; x4z9arb backdoor
C. x4z9arb backdoor; http://x4z9arb.cn/4712/
D. malware; malware–162d917e-766f-4611-b5d6-652791454fca
E. stix; `http://x4z9arb.cn/4712/\’
Correct Answer: D
Question 14:
An investigator is analyzing an attack in which malicious files were loaded on the network and were undetected. Several of the images received during the attack include repetitive patterns. Which anti-forensic technique was used?
A. spoofing
B. obfuscation
C. tunneling
D. steganography
Correct Answer: D
Question 15:
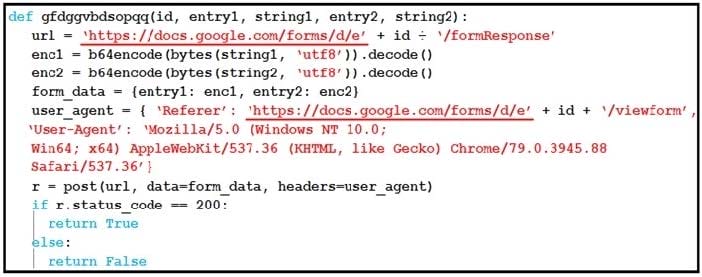
Refer to the exhibit. Which type of code is being used?
A. Shell
B. VBScript
C. BASH
D. Python
Correct Answer: D
Pass4itSure Cisco 300-215 Exam Practice Questions: 59 QAs https://www.pass4itsure.com/300-215.html
The 300-220 exam practice questions will be shared later, and they are being prepared, so stay tuned…
What you can do after you get the certification
Those who earn this credential can work in the following jobs: Cybersecurity Engineer, Cybersecurity Investigator, Incident Manager, Incident Responder, and SOC Analyst.
Washington, D.C., Cisco certification CyberOps Professional has the highest salary
As far as I know, the average salary for Cisco Certified CyberOps Professional certification holders is expected to be $82,778. That’s $30.49 per hour. You can look at the following set of data:
Data from PayScale, a well-known IT-related payroll resource.
Washington, D.C. $89, 246
Atlanta, GA $78,452
New York City $76,586
Austin, TX $78,009
Dallas, TX $73,250
Looking at the above data, you can see that Washington, D.C. has the highest salary level, and you can travel to the area for employment if you want to pay well.
Write at the end:
Follow the path above to get the Cisco certified CyberOps Professional correctly, pass the core exam first, and then go to the centralized exam that you are most likely to pass, when preparing for the exam, choose Pass4itSure Cisco Certified CyberOps Professional exam practice questions https://www.pass4itsure.com/cyberops-professional.html (PDF+VCE) Define the professional life that suits you best. All the best!
Related
Discover more from Exampass: Collection of Cisco (CCNA, CCNP, Meraki Solutions Specialist, CCDP...) exam questions and answers from Pass4itsure
Subscribe to get the latest posts sent to your email.
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

