Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
Here you will find the latest Cisco 350-401 actual exam questions for free! Download free 350-401 VCE or PDF for Cisco 3350-401 test (From Pass4itSure.com), which help you prepare for Cisco 350-401 exam. Get the full Pass4itSure 350-401 dumps to visit https://www.pass4itsure.com/350-401.html (Updated: Jul 21, 2021).
Free PDF download | Cisco 350-401 exam questions
[Latest 350-401 pdf] Cisco 350-401 PDF free download https://drive.google.com/file/d/1B6a-CwlDFp9aaVPE9x5K5ppRhpLZeKv3/view?usp=sharing
Latest Cisco 350-401 exam questions for free
QUESTION 1
An engineer must configure a GRE tunnel interface in the default mode. The engineer has assigned an IPv4 address on
the tunnel and sourced the tunnel from an ethernet interface. Which additional configuration must be made on the tunnel
interface?
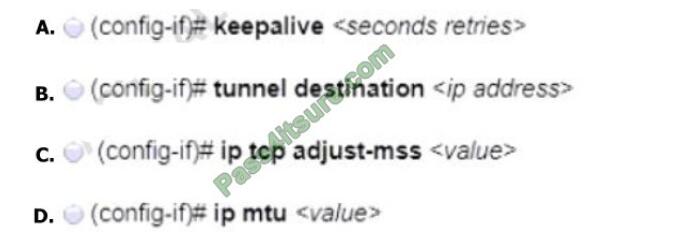
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: B
QUESTION 2
What is provided by the Stealthwatch component of the Cisco Cyber Threat Defense solution?
A. real-time threat management to stop DDoS attacks to the core and access networks
B. real-time awareness of users, devices and traffic on the network
C. malware control
D. dynamic threat control for web traffic
Correct Answer: B
Cisco Stealthwatch is a comprehensive, network telemetry-based, security monitoring and analytics solution that
streamlines incident response through behavioral analysis; detecting denial of service attacks, anomalous behaviour,
malicious
activity and insider threats. Based on a scalable enterprise architecture, Stealthwatch provides near real-time situational
awareness of all users and devices on the network.
Reference: https://www.endace.com/cisco-stealthwatch-solution-brief.pdf
Note: Although answer A seems to be correct but in fact, Stealthwatch does not provide real-time protection for DDoS
attack. It just helps detect DDoS attack only.
Stealthwatch aggregates observed network activity and performs behavioral and policy driven analytics against what it
sees in order to surface problematic activities. While we don\\’t position our self as a DDOS solution, we’re going to
leverage our analytical capabilities to identify a DDoS attack against an internal host using the WebUI.
Reference: https://www.ciscolive.com/c/dam/r/ciscolive/us/docs/2016/pdf/LTRSEC-8421-LG.pdf
QUESTION 3
An engineer measures the Wi-Fi coverage at a customer site. The RSSI values are recorded as follows:
Location A: -72 dBm Location B: -75 dBm Location C: -65 dBm Location D: -80 dBm
Which two statemets does the engineer use to explain these values to the customer? (Choose two)
A. The signl strength at location B is 10 dB better than location C
B. Location D has the strongest RF signal strength.
C. The signal strength at location C is too weak to support web surfing.
D. The RF signal strength at location B is 50% weaker than location A
E. The RF signal strength at location C is 10 times stronger than location B
Correct Answer: DE
QUESTION 4
What is the result of applying this access control list?
ip access-list extended STATEFUL10 permit tcp any any established20 deny ip any any
A. TCP traffic with the URG bit set is allowed
B. TCP traffic with the SYN bit set is allowed
C. TCP traffic with the ACK bit set is allowed
D. TCP traffic with the DF bit set is allowed
Correct Answer: C
The established keyword is only applicable to TCP access list entries to match TCP segments that have the ACK and/or
RST control bit set (regardless of the source and destination ports), which assumes that a TCP connection has already
been established in one direction only. Let\\’s see an example below:
QUESTION 5
Refer to the exhibit.
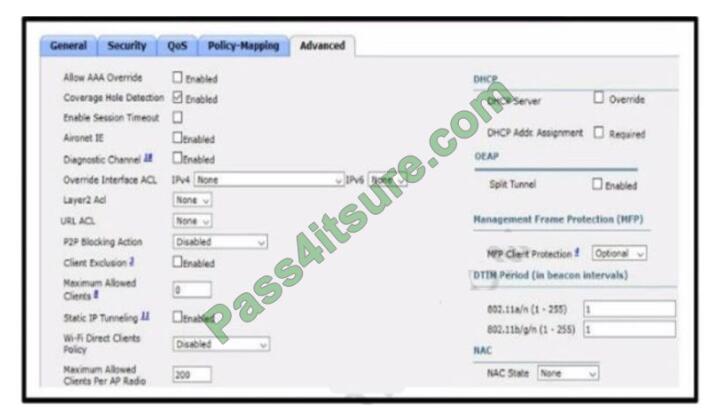
An engineer is investigating why guest users are able to access other guest user devices when the users are connected
to the customer guest WLAN. What action resolves this issue?
A. implement MFP client protection
B. implement split tunneling
C. implement P2P blocking
D. implement Wi-Fi direct policy
Correct Answer: D
QUESTION 6
Refer to the exhibit.
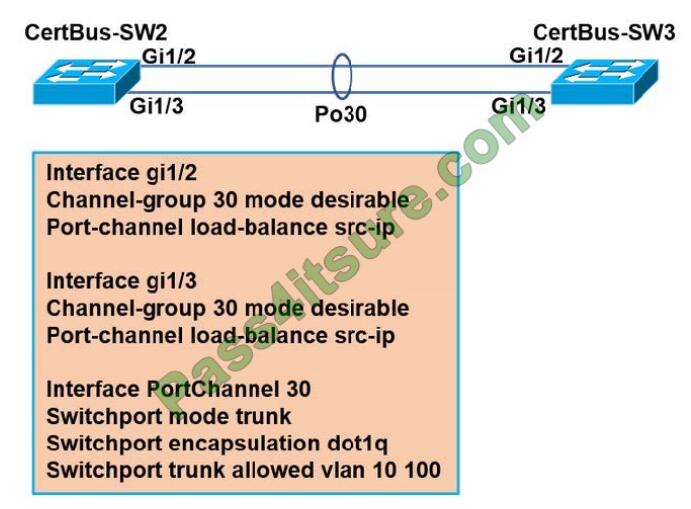
A port channel is configured between SW2 and SW3. SW2 is not running a Cisco operating system. When all physical
connections are made, the port channel does not establish. Based on the configuration except of SW3, what is the
cause of the problem?
A. The port channel on SW2 is using an incompatible protocol.
B. The port-channel trunk is not allowing the native VLAN.
C. The port-channel should be set to auto.
D. The port-channel interface lead balance should be set to src-mac
Correct Answer: A
The Cisco switch was configured with PAgP, which is a Cisco proprietary protocol so non-Cisco switch could not
communicate.
QUESTION 7
A server running Linux is providing support for virtual machines along with DNS and DHCP services for a small
business. Which technology does this represent?
A. container
B. Type 1 hypervisor
C. hardware pass-thru
D. Type 2 hypervisor
Correct Answer: D
In contrast to type 1 hypervisor, a type 2 hypervisor (or hosted hypervisor) runs on top of an operating system and not
the physical hardware directly. A big advantage of Type 2 hypervisors is that management console software is not
required. Examples of type 2 hypervisor are VMware Workstation (which can run on Windows, Mac and Linux) or
Microsoft Virtual PC (only runs on Windows).
QUESTION 8
Which measurement is used from a post wireless survey to depict the cell edge of the access points?
A. SNR
B. Noise
C. RSSI
D. CCI
Correct Answer: A
QUESTION 9
Which two statements about HSRP are true? (Choose two)
A. It supports unique virtual MAC addresses
B. Its virtual MAC is 0000.0C07.ACxx
C. Its default configuration allows for pre-emption
D. It supports tracking
E. Its multicast virtual MAC is 0000.5E00.01xx
Correct Answer: BD
QUESTION 10
Refer to the exhibit. An engineer must assign an IP address of 192.168.1.1/24 to the GigabitEthemet1 interface. Which
two commands must be added to the existing configuration to accomplish this task? (Choose two)
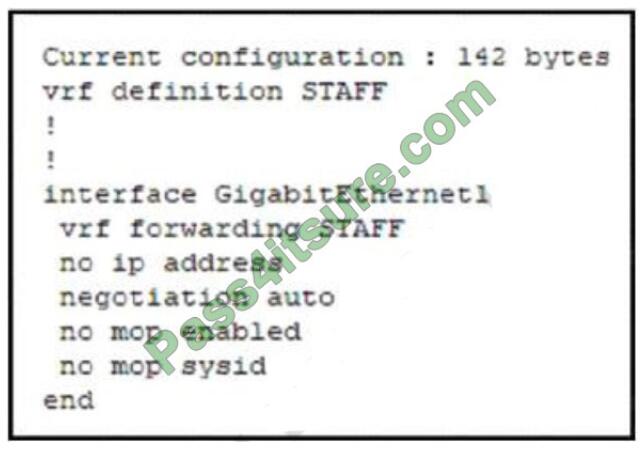
A. Router(config-vrf)#address-family ipv6
B. Router(config-if)Cip address 192.168.1.1 255.255.255.0
C. Router(config-vrf)Sip address 192.168.1.1 255.255.255.0
D. Router(config-if)=address-family ipv4
E. Router(config-vrf)#address-family ipv4
Correct Answer: BE
QUESTION 11
Which standard access control entry permits traffic from odd-numbered hosts in the 10.0.0.0/24 subnet?
A. permit 10.0.0.0 0.0.0.1
B. permit 10.0.0.1 0.0.0.254
C. permit 10.0.0.1 0.0.0.0
D. permit 10.0.0.0 255.255.255.254
Correct Answer: B
QUESTION 12
Refer to exhibit.
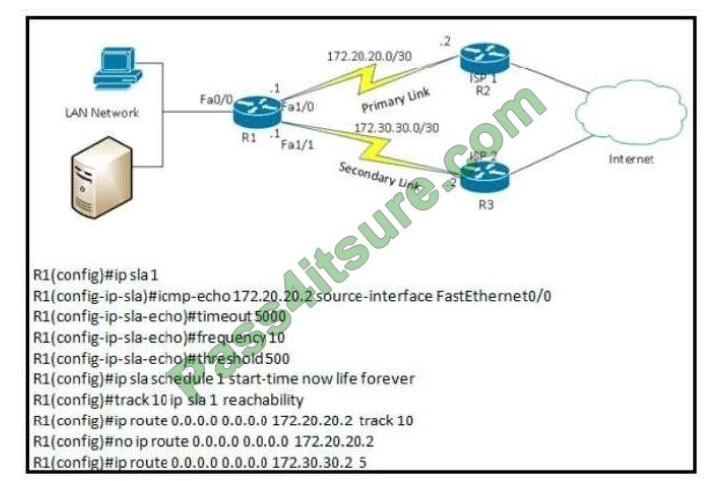
What are two reasons for IP SLA tracking failure? (Choose two )
A. The destination must be 172.30 30 2 for icmp-echo
B. The threshold value is wrong
C. A route back to the R1 LAN network is missing in R2
D. The source-interface is configured incorrectly.
E. The default route has the wrong next hop IP address
Correct Answer: CD Timeout (in milliseconds) sets the amount of time an IP SLAs operation waits for a response from its request packet. In other words, the timeout specifies how long the router should wait for a response to its ping before it is considered
failed.Threshold (in milliseconds too) sets the upper threshold value for calculating network monitoring statistics created
by an IP SLAs operation. Threshold is used to activate a response to IP SLA violation, e.g. send SNMP trap or start
secondary SLA operation. In other words, the threshold value is only used to indicate over threshold events, which do
not affect reachability but may be used to evaluate the proper settings for the timeout command.
For reachability tracking, if the return code is OK or OverThreshold, reachability is up; if not OK, reachability is down.
This tutorial can help you revise IP SLA tracking topic:
http://www.firewall.cx/cisco-technical-knowledgebase/cisco-routers/813-cisco-router-ipslabasic.html
Note: Maybe some of us will wonder why there are these two commands:
R1(config)#ip route 0.0.0.0 0.0.0.0 172.20.20.2 track 10
R1(config)#no ip route 0.0.0.0 0.0.0.0 172.20.20.2
In fact the two commands:
ip route 0.0.0.0 0.0.0.0 172.20.20.2 track 10
ip route 0.0.0.0 0.0.0.0 172.20.20.2
are different. These two static routes can co-exist in the routing table. Therefore if the tracking goes down, the first
command will be removed but the second one still exists and the backup path is not preferred. So we have to remove
the
second one.
QUESTION 13
What are two benefits of YANG? (Choose two.)
A. It enables multiple leaf statements to exist within a leaf list
B. It collects statistical constraint analysis information.
C. It enforces configuration constraints.
D. It enforces configuration semantics.
E. It enforces the use of a specific encoding format for NETCONF
Correct Answer: BE
Pass4itSure Cisco 350-401 exam discount code

PS.
These free practice questions will help you test your knowledge of content from the Cisco 350-401 exam. Pass4itSure has updated new 350-401 dumps questions to help candidates prepare for the 350-401 exam well. get latest dumps for 350-401: https://www.pass4itsure.com/350-401.html (350-401 Dumps PDF, VCE Q&As: 544).
Pass4itsure Cisco CCNP
free 300-815 exam questions https://www.exampass.net/latest-cisco-300-815-actual-exam-questions-for-free-300-815-exam-discount.html
free 300-615 exam questions https://www.exampass.net/latest-cisco-300-615-actual-exam-questions-for-free-300-615-exam-discount.html
free 300-610 exam questions https://www.exampass.net/latest-cisco-300-610-actual-exam-questions-for-free-300-610-exam-discount.html
Related
Discover more from Exampass: Collection of Cisco (CCNA, CCNP, Meraki Solutions Specialist, CCDP...) exam questions and answers from Pass4itsure
Subscribe to get the latest posts sent to your email.
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

