Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
Pass4itsure share these resources with you. Both VCE and PDF dumps contain the latest CompTIA SY0-501 exam questions, which will ensure your SY0-501 exam 100% passed! You can get SY0-501 VCE dumps and SY0-501 PDF dumps from Pass4itsure. Please get the latest Pass4itsure SY0-501 dumps here: https://www.pass4itsure.com/sy0-501.html (1139 QA Dumps).
Download The Real CompTIA SY0-501 PDF Here, Free
[free pdf] CompTIA SY0-501 PDF [Drive] https://drive.google.com/file/d/1AxGkPPFaVn6ENVvhk5YmorFwV1eWzdRS/view?usp=sharing
CompTIA SY0-501 Practice Test Questions Answers
QUESTION 1
A company has a data classification system with definitions for “Private” and “Public”. The company\\’s security policy
outlines how data should be protected based on type. The company recently added the data type “Proprietary”. Which
of the following is the MOST likely reason the company added this data type?
A. Reduced cost
B. More searchable data
C. Better data classification
D. Expanded authority of the privacy officer
Correct Answer: C
QUESTION 2
A company hires a third-party firm to conduct an assessment of vulnerabilities exposed to the Internet. The firm informs
the company that an exploit exists for an FTP server that had a version installed from eight years ago. The company
has
decided to keep the system online anyway, as no upgrade exists from the vendor.
Which of the following BEST describes the reason why the vulnerability exists?
A. Default configuration
B. End-of-life system
C. Weak cipher suite
D. Zero-day threats
Correct Answer: B
QUESTION 3
When a malicious user is able to retrieve sensitive information from RAM, the programmer has failed to implement:
A. session keys.
B. encryption of data at rest
C. encryption of data in use.
D. ephemeral keys.
Correct Answer: C
Compromising data in use enables access to encrypted data at rest and data in motion. For example, someone with access to random access memory (RAM) can parse that memory to locate the encryption key for data at rest. Once they
have obtained that encryption key, they can decrypt encrypted data at rest.
QUESTION 4
An attacker discovers a new vulnerability in an enterprise application. The attacker takes advantage of the vulnerability
by developing new malware. After installing the malware, the attacker is provided with access to the infected machine.
Which of the following is being described?
A. Zero-day exploit
B. Remote code execution
C. Session hijacking
D. Command injection
Correct Answer: A
QUESTION 5
A company wants to deploy PKI on its Internet-facing website. The applications that are currently deployed are:
1.
www company com (mam website)
2.
contact us company com (for locating a nearby location)
3.
quotes company com (for requesting a price quote)
The company wants to purchase one SSL certificate that will work for all the existing applications and any future
applications that follow the same naming conventions, such as store company com. Which of the following certificate
types would BEST meet the requirements?
A. SAN
B. Wildcard
C. Extended validation
D. Self-signed
Correct Answer: B
QUESTION 6
A penetration tester is checking to see if an internal system is vulnerable to an attack using a remote listener. Which of
the following commands should the penetration tester use to verify if this vulnerability exists? (Choose two.)
A. tcpdump
B. nc
C. nmap
D. nslookup
E. tail
F. tracert
Correct Answer: BC
QUESTION 7
A security analyst is reviewing the following packet capture of an attack directed at a company\\’s server located in the
DMZ:
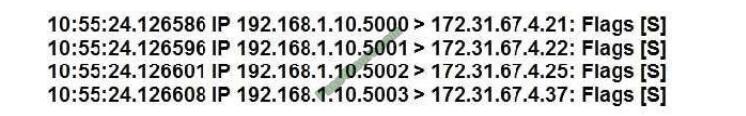
Which of the following ACLs provides the BEST protection against the above attack and any further attacks from the
the same IP, while minimizing service interruption?
A. DENY TCO From ANY to 172.31.64.4
B. Deny UDP from 192.168.1.0/24 to 172.31.67.0/24
C. Deny IP from 192.168.1.10/32 to 0.0.0.0/0
D. Deny TCP from 192.168.1.10 to 172.31.67.4
Correct Answer: D
QUESTION 8
Corporations choose to exceed regulatory framework standards because of which of the following incentives?
A. It improves the legal defensibility of the company.
B. It gives a social defense that the company is not violating customer privacy laws.
C. It proves to investors that the company takes APT cyber actors seriously
D. It results in overall industrial security standards being raised voluntarily.
Correct Answer: A
QUESTION 9
An employee in the finance department receives an email, which appears to come from the Chief Financial Officer
(CFO), instructing the employee to immediately wire a large sum of money to a vendor. Which of the following BEST
describes the principles of social engineering used? (Choose two.)
A. Familiarity
B. Scarcity
C. Urgency
D. Authority
E. Consensus
Correct Answer: CD
QUESTION 10
A stock trading company had the budget for enhancing its secondary datacenter approved. Since the main site is a
hurricane-affected area and the disaster recovery site is 100 mi (161 km) away, the company wants to ensure its
business is always operational with the least amount of man-hours needed. Which of the following types of disaster
recovery sites should the company implement?
A. Hot site
B. Warm site
C. Cold site
D. Cloud-based site
Correct Answer: D
QUESTION 11
Which of the following enables sniffing attacks against a switched network?
A. ARP poisoning
B. IGMP snooping
C. IP spoofing
D. SYN flooding
Correct Answer: A
QUESTION 12
A cryptographer has developed a new proprietary hash function for a company and solicited employees to test the
function before recommending its implementation. An employee takes the plaintext version of a document and hashes
it, then changes the original plaintext document slightly and hashes it, and continues repeating this process until two
identical hash values are produced from two different documents. Which of the following BEST describes this
cryptographic attack?
A. Brute force
B. Known plaintext
C. Replay
D. Collision
Correct Answer: D
QUESTION 13
Which of the following is a major difference between XSS attacks and remote code exploits?
A. XSS attacks use machine language, while remote exploits use interpreted language
B. XSS attacks target servers, while remote code exploits target clients
C. Remote code exploits aim to escalate attackers\\’ privileges, while XSS attacks aim to gain access only
D. Remote code exploits allow writing code at the client-side and executing it, while XSS attacks require no code to
work
Correct Answer: A
Pass4itsure Discount Code 2020

P.S
Exampass shares all the resources: Latest CompTIA SY0-501 practice questions, latest SY0-501 pdf dumps, SY0-501 exam video learning. CompTIA SY0-501 dumps https://www.pass4itsure.com/sy0-501.html has come to help you prepare for the implementation of the CompTIA SY0-501 exam and its comprehensive and thorough SY0-501 exam practice materials, which will help you successfully pass the examination.
Related
Discover more from Exampass: Collection of Cisco (CCNA, CCNP, Meraki Solutions Specialist, CCDP...) exam questions and answers from Pass4itsure
Subscribe to get the latest posts sent to your email.
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

