Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
Hey guys, this blog is just about sharing your experience with the Cisco CCNP 350-701 SCOR exam and some free 350-701 SCOR exam resources. Passing the 350-701 exam requires focusing most of your studies on the 350-701 practice exam, practicing it over and over again, and memorizing knowledge points. It’s not a waste of time, it’s the right way to learn.
The 350-701 practice exam is highly recommended for >>> https://www.pass4itsure.com/350-701.html authentic 350-701 exam questions and answers. (350-701 SCOR Dumps PDF+ VCE)
Share your experience and get the address, and then share the latest 350-701 SCOR exam study materials, for free!
First, Cisco Security Core Technologies 350-701 SCOR practice exam online
QUESTION 1
Which service allows a user to export application usage and performance statistics with Cisco Application Visibility and
control?
A. SNORT
B. NetFlow
C. SNMP
D. 802.1X
Correct Answer: B
Application Visibility and Control (AVC) supports NetFlow to export application usage and performance statistics. This
data can be used for analytics, billing, and security policies.
QUESTION 2
What is the purpose of the certificate signing request when adding a new certificate for a server?
A. It is the password for the certificate that is needed to install it.
B. It provides the server information so a certificate can be created and signed
C. It provides the certificate client information so the server can authenticate against it when installing
D. It is the certificate that will be loaded onto the server
Correct Answer: B
A certificate signing request (CSR) is one of the first steps towards getting your own SSL Certificate. Generated on the
same server you plan to install the certificate on, the CSR contains information (e.g. common name, organization,
country) that the Certificate Authority (CA) will use to create your certificate. It also contains the public key that will be
included in your certificate and is signed with the corresponding private key
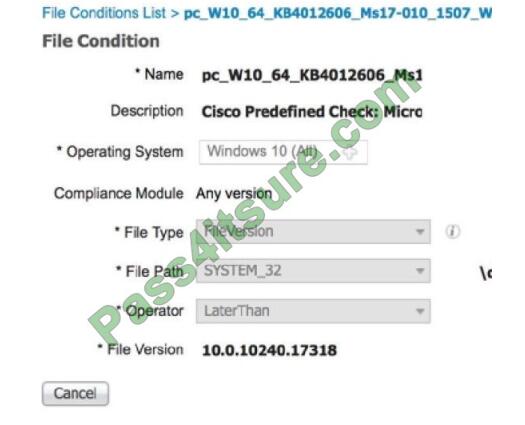
QUESTION 3
An engineer used a posture check on a Microsoft Windows endpoint and discovered that the MS17-010 patch was not
installed, which left the endpoint vulnerable to WannaCry ransomware. Which two solutions mitigate the risk of this
ransomware infection? (Choose two)
A. Configure a posture policy in Cisco Identity Services Engine to install the MS17-010 patch before allowing access on
the network.
B. Set up a profiling policy in Cisco Identity Service Engine to check and endpoint patch level before allowing access on
the network.
C. Configure a posture policy in Cisco Identity Services Engine to check that an endpoint patch level is met before
allowing access to the network.
D. Configure endpoint firewall policies to stop the exploit traffic from being allowed to run and replicate throughout the network.
E. Set up a well-defined endpoint patching strategy to ensure that endpoints have critical vulnerabilities patched in a
timely fashion.
Correct Answer: AC
A posture policy is a collection of posture requirements, which are associated with one or more identity groups, and
operating systems. We can configure ISE to check for the Windows patch at Work Centers > Posture > Posture
Elements > Conditions > File.In this example, we are going to use the predefined file check to ensure that our Windows
10 clients have the critical security patch installed to prevent the Wanna Cry malware.
QUESTION 4
Which two capabilities does TAXII support? (Choose two)
A. Exchange
B. Pull messaging
C. Binding
D. Correlation
E. Mitigating
Correct Answer: BC
The Trusted Automated exchange of Indicator Information (TAXII) specifies mechanisms for exchanging structured cyber threat information between parties over the network.TAXII exists to provide specific capabilities to those interested in sharing structured cyber threat information.
TAXII Capabilities are the highest level at which TAXII actions can be described. There are three capabilities that this version of TAXII supports: push messaging, pull messaging, and discovery.Although there is no “binding” capability in the list it is the best answer here.
QUESTION 5
What is the result of running the crypto isakmp key ciscXXXXXXXX address 172.16.0.0 command?
A. authenticates the IKEv2 peers in the 172.16.0.0/16 range by using the key ciscXXXXXXXX
B. authenticates the IP address of the 172.16.0.0/32 peer by using the key ciscXXXXXXXX
C. authenticates the IKEv1 peers in the 172.16.0.0/16 range by using the key ciscXXXXXXXX
D. secures all the certificates in the IKE exchange by using the key ciscXXXXXXXX
Correct Answer: A
QUESTION 6
What is managed by Cisco Security Manager?
A. access point
B. WSA
C. ASA
D. ESA
Correct Answer: C
Reference: https://www.cisco.com/c/en/us/products/security/security-manager/index.html
QUESTION 7
What is a benefit of using Cisco FMC over Cisco ASDM?
A. Cisco FMC uses Java while Cisco ASDM uses HTML5.
B. Cisco FMC provides centralized management while Cisco ASDM does not.
C. Cisco FMC supports pushing configurations to devices while Cisco ASDM does not.
D. Cisco FMC supports all firewall products whereas Cisco ASDM only supports Cisco ASA devices
Correct Answer: B
QUESTION 8
An organization recently installed a Cisco WSA and would like to take advantage of the AVC engine to allow the
organization to create a policy to control application-specific activity. After enabling the AVC engine, what must be done to implement this?
A. Use security services to configure the traffic monitor,
B. Use URL categorization to prevent application traffic.
C. Use an access policy group to configure application control settings.
D. Use web security reporting to validate engine functionality
Correct Answer: C
The Application Visibility and Control (AVC) engine lets you create policies to control application activity on the network without having to fully understand the underlying technology of each application. You can configure application control settings in Access Policy groups. You can block or allow applications individually or according to application type. You can also apply controls to particular application types.
QUESTION 9
Which two statements about a Cisco WSA configured in Transparent mode are true? (Choose two)
A. It can handle explicit HTTP requests.
B. It requires a PAC file for the client web browser.
C. It requires a proxy for the client web browser.
D. WCCP v2-enabled devices can automatically redirect traffic destined to port 80.
E. Layer 4 switches can automatically redirect traffic destined to port 80.
Correct Answer: DE
QUESTION 10
Refer to the exhibit. A network engineer is testing NTP authentication and realizes that any device synchronizes time
with this router and that NTP authentication is not enforced. What is the cause of this issue?
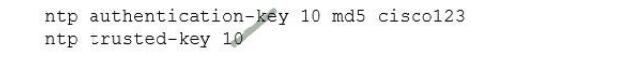
A. The hashing algorithm that was used as MD5, which is unsupported.
B. The key was configured in plain text.
C. NTP authentication is not enabled.
D. The router was not rebooted after the NTP configuration was updated.
Correct Answer: C
QUESTION 11
An engineer is configuring AMP for endpoints and wants to block certain files from executing. Which outbreak control
the method is used to accomplish this task?
A. device flow correlation
B. simple detections
C. application blocking list
D. advanced custom detections
Correct Answer: C
QUESTION 12
Refer to the exhibit.
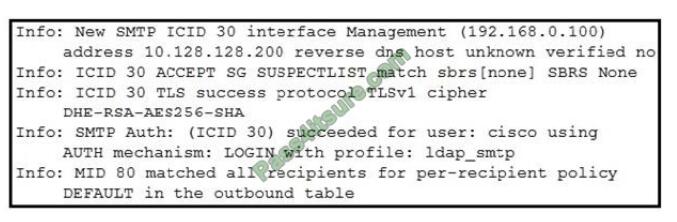
Which type of authentication is in use?
A. LDAP authentication for Microsoft Outlook
B. POP3 authentication
C. SMTP relay server authentication
D. external user and relay mail authentication
Correct Answer: D
The exhibit in this Question shows a successful TLS connection from the remote host (reception) in the mail log.
QUESTION 13
What is the difference between FlexVPN and DMVPN?
A. DMVPN uses IKEv1 or IKEv2, FlexVPN only uses IKEv1
B. DMVPN uses only IKEv1 FlexVPN uses only IKEv2
C. FlexVPN uses IKEv2, DMVPN uses IKEv1 or IKEv2
D. FlexVPN uses IKEv1 or IKEv2, DMVPN uses only IKEv2
Correct Answer: C
Second, Cisco 350-701 SCOR pdf download
350-701 SCOR dumps pdf https://drive.google.com/file/d/1ayHc-HIUTc0eLVh2e_CjfseaTK-LJkcK/view?usp=sharing
Ending:
The 350-701 practice exam should be thoroughly studied, and more time should be spent practicing the 350-701 practice test! Another tip: To test your true understanding of the topic, ask yourself some questions. Overall, the 350-701 exam is very difficult to learn, and there are too many questions to know, and it is difficult to remember them all. But I think if you follow my advice, you should be able to get through!
Start here with the 350-701 practice exam >>> https://www.pass4itsure.com/350-701.html
Related
Discover more from Exampass: Collection of Cisco (CCNA, CCNP, Meraki Solutions Specialist, CCDP...) exam questions and answers from Pass4itsure
Subscribe to get the latest posts sent to your email.
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

