Cisco Certification Exam Prep Materials
Cisco CCNA Exam Prep Material Download
Cisco CCT Exam Prep Material Download
- Cisco 010-151 Dumps PDF
- Cisco 100-490 Dumps PDF
- Cisco 100-890 Dumps PDF
- Tips: Beginning February 10, the CCT Certification 500-150 FLDTEC v1.0 exam will replace the 100-490, 010-151, and 100-890 exams.
Cisco CyberOps Exam Prep Material Download
Cisco DevNet Exam Prep Material Download
Cisco CCNP Exam Prep Material Download
- Cisco 300-410 Dumps PDF
- Cisco 300-415 Dumps PDF
- Cisco 300-420 Dumps PDF
- Cisco 300-425 Dumps PDF
- Cisco 300-430 Dumps PDF
- Cisco 300-435 Dumps PDF
- Cisco 300-440 Dumps PDF
- Cisco 300-510 Dumps PDF
- Cisco 300-515 Dumps PDF
- Cisco 300-535 Dumps PDF
- Cisco 300-610 Dumps PDF
- Cisco 300-615 Dumps PDF
- Cisco 300-620 Dumps PDF
- Cisco 300-630 Dumps PDF
- Cisco 300-635 Dumps PDF
- Cisco 300-710 Dumps PDF
- Cisco 300-715 Dumps PDF
- Cisco 300-720 Dumps PDF
- Cisco 300-725 Dumps PDF
- Cisco 300-730 Dumps PDF
- Cisco 300-735 Dumps PDF
- Cisco 300-810 Dumps PDF
- Cisco 300-815 Dumps PDF
- Cisco 300-820 Dumps PDF
- Cisco 300-835 Dumps PDF
Cisco CCIE Exam Prep Material Download
- Cisco 350-401 Dumps PDF
- Cisco 350-501 Dumps PDF
- Cisco 350-601 Dumps PDF
- Cisco 350-701 Dumps PDF
- Cisco 350-801 Dumps PDF
Cisco CCDE Exam Prep Material Download
Cisco Other Exam Prep Material Download
- Cisco 500-052 Dumps PDF
- Cisco 500-210 Dumps PDF
- Cisco 500-220 Dumps PDF
- Cisco 500-420 Dumps PDF
- Cisco 500-442 Dumps PDF
- Cisco 500-444 Dumps PDF
- Cisco 500-470 Dumps PDF
- Cisco 500-490 Dumps PDF
- Cisco 500-560 Dumps PDF
- Cisco 500-710 Dumps PDF
- Cisco 700-150 Dumps PDF
- Cisco 700-750 Dumps PDF
- Cisco 700-760 Dumps PDF
- Cisco 700-765 Dumps PDF
- Cisco 700-805 Dumps PDF
- Cisco 700-821 Dumps PDF
- Cisco 700-826 Dumps PDF
- Cisco 700-846 Dumps PDF
- Cisco 700-905 Dumps PDF
- Cisco 820-605 Dumps PDF
Fortinet Exam Dumps
fortinet nse4_fgt-6.4 dumps (pdf + vce)
fortinet nse4_fgt-6.2 dumps (pdf + vce)
fortinet nse5_faz-6.4 dumps (pdf + vce)
fortinet nse5_faz-6.2 dumps (pdf + vce)
fortinet nse5_fct-6.2 dumps (pdf + vce)
fortinet nse5_fmg-6.4 dumps (pdf + vce)
fortinet nse5_fmg-6.2 dumps (pdf + vce)
fortinet nse6_fml-6.2 dumps (pdf + vce)
fortinet nse6_fnc-8.5 dumps (pdf + vce)
fortinet nse7_efw-6.4 dumps (pdf + vce)
fortinet nse7_efw-6.2 dumps (pdf + vce)
fortinet nse7_sac-6.2 dumps (pdf + vce)
fortinet nse7_sdw-6.4 dumps (pdf + vce)
fortinet nse8_811 dumps (pdf + vce)
Want to know how others passed the Cisco ENCOR 350-401 exam? If you’re interested, I’ll post my understanding of the SC-300 exam here. Note! I recommend that everyone learns about the new Cisco CCNP 350-401 study guide dump, the 350-401 study guide has a complete learning material that you can follow along with the exercises, find the way, use the right force, and you will be able to succeed.
To view all the 350-401 study guides, check here https://www.pass4itsure.com/350-401.html
What preparation material do you use to prepare for 350-401?
Want to get into the Cisco CCNP field, but are struggling to find good resources or examples of learning materials to get there, there are many 350-401 learning materials, but you want the most useful. I recommend the Pass4itSure 350-401 exam dumps with 350-401 exam questions and answers, 350-401 PDF, 350-401 VCE, 350-401 test. The most popular 350-401 study materials!
Cisco 350-401 study guide ENCOR pdf (latest)
google drive: 350-401 ENCOR pdf free https://drive.google.com/file/d/1YOF1zCZRaoX3sgUdpVvgwSRlRkj0pt_R/view?usp=sharing
Learning Cisco 350-401 ENCOR certification test question
QUESTION 1
Refer to the exhibit.

What is the effect of this configuration?
A. The device will allow users at 192.168.0.202 to connect to vty lines 0 through 4 using the password ciscotestkey
B. The device will allow only users at 192 168.0.202 to connect to vty lines 0 through 4
C. When users attempt to connect to vty lines 0 through 4. the device will authenticate them against TACACS* if local
authentication fails
D. The device will authenticate all users connecting to vty lines 0 through 4 against TACACS+
Correct Answer: D
QUESTION 2
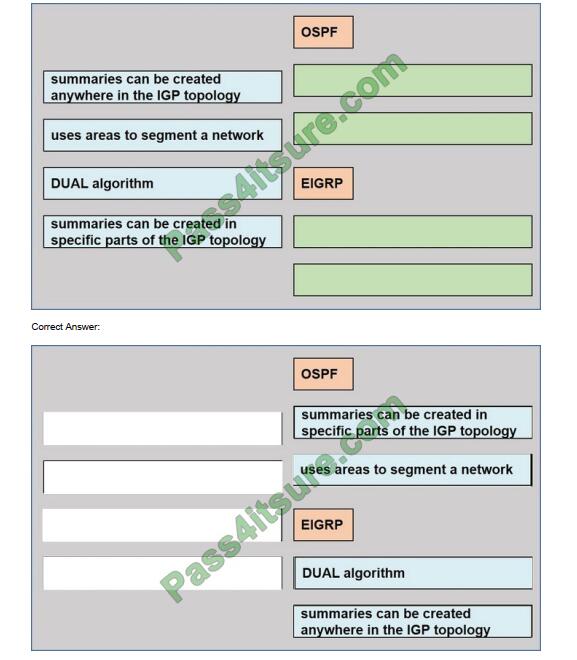
DRAG-DROP
Drag the drop the description from the left onto the routing protocol they describe on the right.
Select and Place:
QUESTION 3
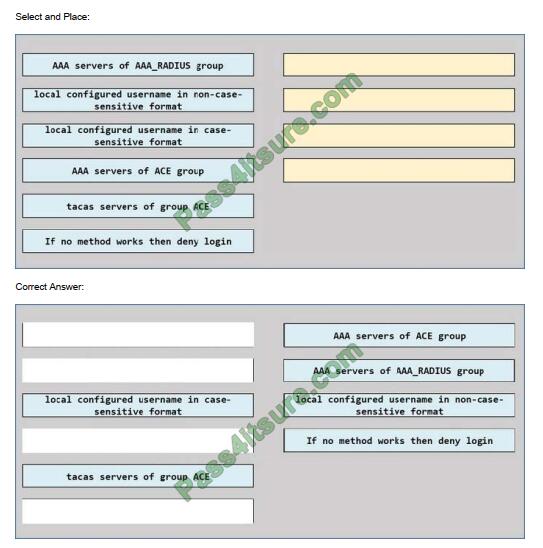
An engineer creates the configuration below. Drag and drop the authentication methods from the left into the order of
priority on the right. Not all options are used.
R1#sh run | i aaaaaa new-model aaa authentication login default group ACE group AAA_RADIUS local-cassava
session-id common
R1#
Select and Place:
QUESTION 4
Refer to the exhibit.
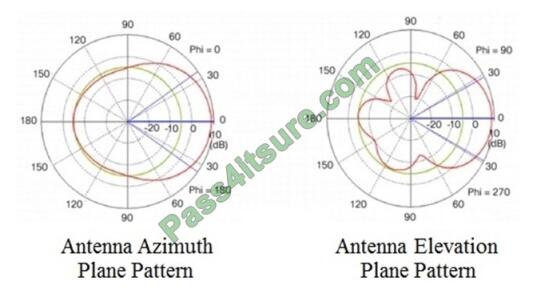
Which type of antenna do the radiation patterns present?
A. Patch B. Omnidirectional
C. Yagi
D. Dipole
Correct Answer: A
QUESTION 5
Which component of the Cisco Cyber Threat Defense solution provides user and flow context analysis?
A. Cisco Firepower and FireSIGHT
B. Cisco Stealthwatch system
C. Advanced Malware Protection
D. Cisco Web Security Appliance
Correct Answer: B
The goal of the Cyber Threat Defense solution is to introduce a design and architecture that can help facilitate the
discovery, containment, and remediation of threats once they have penetrated into the network interior. Cisco Cyber
Threat Defense version 2.0 makes use of several solutions to accomplish its objectives:
NetFlow and the Lancope StealthWatch System
1.
Broad visibility
2.
User and flow context analysis
3.
Network behavior and anomaly detection
4.
Incident response and network forensics
Cisco FirePOWER and FireSIGHT
1.
Real-time threat management
2.
Deeper contextual visibility for threats bypassing the perimeters?URL control
Advanced Malware Protection (AMP)
1.
Endpoint control with AMP for Endpoints
2.
Malware control with AMP for networks and content
Content Security Appliances and Services
1.
Cisco Web Security Appliance (WSA) and Cloud Web Security (CWS)
2.
Dynamic threat control for web traffic
3.
Latest 350-401 Dumps | 350-401 Study Guide | 350-401 Exam Questions 6 / 13https://www.pass4itsure.com/350-401.html
2021 Latest pass4itsure 350-401 PDF and VCE dumps Download
Outbound URL analysis and data transfer controls
4.
Detection of suspicious web activity
5.
Cisco Email Security Appliance (ESA)
6.
Dynamic threat control for email traffic
7.
Detection of suspicious email activity
Cisco Identity Services Engine (ISE)
1.
User and device identity integration with Lancope StealthWatch
2.
Remediation policy actions using pxGrid
QUESTION 6
A customer has deployed an environment with shared storage to allow for the migration of virtual machines between
servers with dedicated operating systems that provide the virtualization platform.
What is this operating system described as?
A. hosted virtualization
B. type 1 hypervisor
C. container oriented
D. decoupled
Correct Answer: B
QUESTION 7
An engineer must configure an ACL that permits packets that include an ACK In the TCP header. Which entry must be
Included In the ACL?
A. access-list 110 permits tcp any any eq 21 tcp-ack
B. access-list 10 permit ip any any eq 21 tcp-ack
C. access-list 10 permit tcp any any eq 21 established
D. access-list 110 permit tcp any any eq 21 established
Correct Answer: D
QUESTION 8
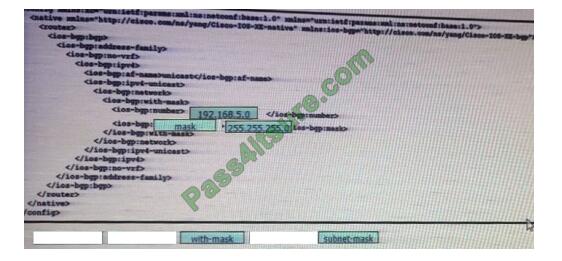
Drag and drop the snippets onto the blanks within the code to construct a script that advertises the network prefox
192.168.5.0 session. Not all options are used.
Select and Place:
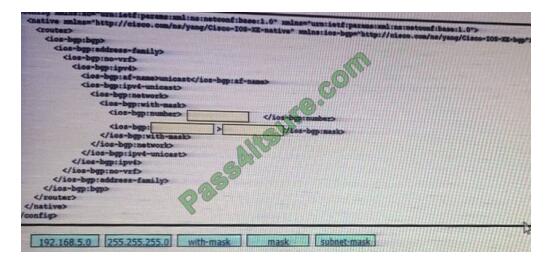
Correct Answer:
QUESTION 9
A customer has recently implemented a new wireless infrastructure using WLC-5520S at a site directly next to a large
commercial airport Users report that they intermittently lose Wi-Fi connectivity, and troubleshooting reveals it is due to
frequent channel changes Which two actions fix this issue? (Choose two)
A. Remove UNII-2 and Extended UNII-2 channels from the 5 GHz channel list
B. Restore the OCA default settings because this automatically avoids channel interference
C. Disable DFS channels to prevent interference writ) Doppler radar
D. Enable DFS channels because they are immune to radar interference
E. Configure channels on the UNII-2 and the Extended UNII-2 sub-bands of the 5 GHz band only
Correct Answer: AC
QUESTION 10
Which two statements about Cisco Express Forwarding load balancing are true? (Choose two)
A. Each hash maps directly to a single entry in the RIB
B. It combines the source IP address subnet mask to create a hash for each destination
C. Cisco Express Forwarding can load-balance over a maximum of two destinations
D. It combines the source and destination IP addresses to create a hash for each destination
E. Each hash maps directly to a single entry in the adjacency table
Correct Answer: DE
Cisco IOS software basically supports two modes of CEF load balancing: On a per-destination or per-packet basis. For predestination load balancing a hash is computed out of the source and destination IP address (-> Answer \’ It combines the source and destination IP addresses to create a hash for each destination\’ is correct).
This hash points to exactly one of the adjacency entries in the adjacency table (-> Answer \’ Each hash maps directly to a single entry in the adjacency table\’ is correct), providing that the same path is used for all packets with this source/destination address pair.
If per-packet load balancing is used the packets are distributed round-robin over the available paths. In either case, the information in the FIB and adjacency tables provide all the necessary forwarding information, just like for non-load balancing operation.
The number of paths used is limited by the number of entries the routing protocol puts in the routing table, the default in IOS is 4 entries for most IP routing protocols with the exception of BGP, where it is one entry. The maximum number that can be configured is 6 different paths -> Answer \’ Cisco Express Forwarding can load-balance over a maximum of two destinations\’ is not correct.
QUESTION 11
What is the function of a control-plane node in a Cisco SD-Access solution?
A. to run a mapping system that manages endpoint to network device relationships
B. to implement policies and communicate with networks outside the fabric
C. to connect external Layer 3 networks to the SD-Access fabric.
D. to connect APs and wireless endpoints to the SD-Access fabric
Correct Answer: A
QUESTION 12
Refer to the exhibit.
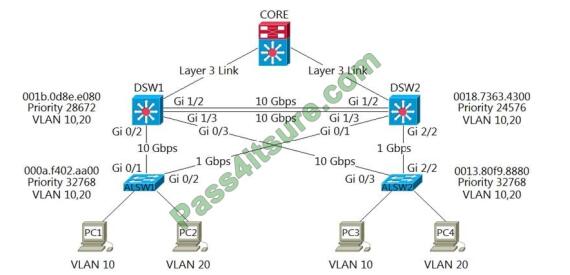
Which two commands ensure that DSW1 becomes the root bridge for VLAN 10? (Choose two.)
A. DSW1(config)#spanning-tree VLAN 10 priority 4096
B. DSW1(config)#spanning-tree VLAN 10 priority root
C. DSW2(config)#spanning-tree VLAN 10 priority 61440
D. DSW1(config)#spanning-tree VLAN 10 port-priority 0
E. DSW2(config)#spanning-tree VLAN 20 priority 0
Correct Answer: AB
QUESTION 13
Refer to the exhibit.
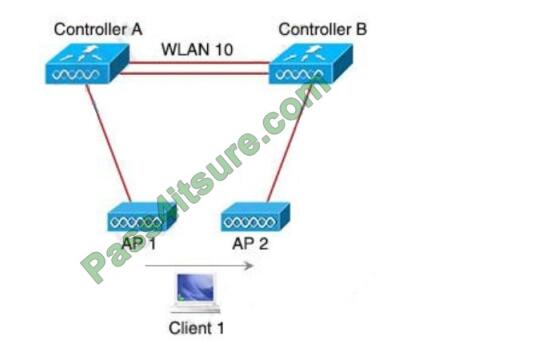
Both controllers are in the same mobility group. Which result occurs when client 1 roams between APs that are
registered to different controllers in the same WLAN?
A. Client 1 contact controller B by using an EoIP tunnel.
B. CAPWAP tunnel is created between controller A and controller B.
C. Client 1 uses an EoIP tunnel to contact controller A.
D. The client database entry moves from controller A to controller B.
Correct Answer: D
This is called Inter Controller-L2 Roaming. Inter-Controller (normally layer 2) roaming occurs when a client roams
between two APs registered to two different controllers, where each controller has an interface in the client subnet. In
In this instance, controllers exchange mobility control messages (over UDP port 16666) and the client database entry is
moved from the original controller to the new controller
The correct Cisco 350-401 study guide key points summarize:
Be sure to remember to follow a lot of practice 350-401 practice tests, find ways to use the right strength, and you will be able to successfully obtain CCNP certification.
Get the Right Cisco 350-401 study guide here: https://www.pass4itsure.com/350-401.html ( 350-401 Dumps PDF +VCE)
Related
Discover more from Exampass: Collection of Cisco (CCNA, CCNP, Meraki Solutions Specialist, CCDP...) exam questions and answers from Pass4itsure
Subscribe to get the latest posts sent to your email.
Written by Ralph K. Merritt
We are here to help you study for Cisco certification exams. We know that the Cisco series (CCNP, CCDE, CCIE, CCNA, DevNet, Special and other certification exams are becoming more and more popular, and many people need them. In this era full of challenges and opportunities, we are committed to providing candidates with the most comprehensive and comprehensive Accurate exam preparation resources help them successfully pass the exam and realize their career dreams. The Exampass blog we established is based on the Pass4itsure Cisco exam dump platform and is dedicated to collecting the latest exam resources and conducting detailed classification. We know that the most troublesome thing for candidates during the preparation process is often the massive amount of learning materials and information screening. Therefore, we have prepared the most valuable preparation materials for candidates to help them prepare more efficiently. With our rich experience and deep accumulation in Cisco certification, we provide you with the latest PDF information and the latest exam questions. These materials not only include the key points and difficulties of the exam, but are also equipped with detailed analysis and question-answering techniques, allowing candidates to deeply understand the exam content and master how to answer questions. Our ultimate goal is to help you study for various Cisco certification exams, so that you can avoid detours in the preparation process and get twice the result with half the effort. We believe that through our efforts and professional guidance, you will be able to easily cope with exam challenges, achieve excellent results, and achieve both personal and professional improvement. In your future career, you will be more competitive and have broader development space because of your Cisco certification.
Categories
2025 Microsoft Top 20 Certification Materials
- Microsoft Azure Administrator –> az-104 dumps
- Microsoft Azure Fundamentals –> az-900 dumps
- Data Engineering on Microsoft Azure –> dp-203 dumps
- Developing Solutions for Microsoft Azure –> az-204 dumps
- Microsoft Power Platform Developer –> pl-400 dumps
- Designing and Implementing a Microsoft Azure AI Solution –> ai-102 dumps
- Microsoft Power BI Data Analyst –> pl-300 dumps
- Designing and Implementing Microsoft DevOps Solutions –> az-400 dumps
- Microsoft Azure Security Technologies –> az-500 dumps
- Microsoft Cybersecurity Architect –> sc-100 dumps
- Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM) –> mb-910 dumps
- Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP) –> mb-920 dumps
- Microsoft Azure Data Fundamentals –> dp-900 dumps
- Microsoft 365 Fundamentals –> ms-900 dumps
- Microsoft Security Compliance and Identity Fundamentals –> sc-900 dumps
- Microsoft Azure AI Fundamentals –> ai-900 dumps
- Microsoft Dynamics 365: Finance and Operations Apps Solution Architect –> mb-700 dumps
- Microsoft 365 Certified: Enterprise Administrator Expert –> ms-102 dumps
- Microsoft 365 Certified: Collaboration Communications Systems Engineer Associate –> ms-721 dumps
- Endpoint Administrator Associate –> md-102 dumps

